Blog
Insights and expertise from Thoropass
Featured
Becoming the End-to-End Cybersecurity Auditor
Innovation has always been at the forefront for Thoropass, and with the introduction of the Audit Lifecycle Platform, we're the only end-to-end cybersecurity auditor built for the AI era.
Latest posts
Pentesting
Thoropass Security Research: React2Shell - When a React Feature Turns Into a Server Takeover
February 5, 2026
|
Muhammad Uwais
In this post, Thoropass pentester Muhammad Uwais explain what React2Shell is, why it matters, and what teams can learn from it, using clear examples and real-world context.
Read more
Compliance automation
Is Your Compliance Platform Making You Audit-Ready … or Just Busy?
January 30, 2026
|
Cristina Bartolacci
Thoropass' Cristina Bartolacci looks at how IT security compliance systems could create more work than they save, and what companies should look for to meaningfully reduce risk.
Read more

AI powered audit
Becoming the End-to-End Cybersecurity Auditor
January 29, 2026
|
Austin Ogilvie, Eva Pittas & Sam Li
Innovation has always been at the forefront for Thoropass, and with the introduction of the Audit Lifecycle Platform, we're the only end-to-end cybersecurity auditor built for the AI era.
Read more
Pentesting
Thoropass Security Research: HikVision Local Privilege Escalation - CVE-2025-39246
January 27, 2026
|
Eduardo Bido
Our penetration testing team outlines three recently identified vulnerabilities, including CVE-2025-39246 and CVE-2025-5007, and how they can be mitigated.
Read more

Audit
The ultimate cyber IT audit glossary for security leaders
January 23, 2026
|
Audits can involve a seemingly endless amount of confusing terms and concepts. We've compiled them all here in one place, to make your next audit easier.
Read more
.png)
AI
Choosing an AI-powered compliance tool: A practitioner’s guide
January 23, 2026
|
Learn how to evaluate AI powered compliance tools, manage data privacy risks, and select a platform that satisfies real-world auditors.
Read more
Audit
10 Things I’ve Learned from Thousands of IT Audits
January 15, 2026
|
Chris Biero
IT audits don't have to cause sleepless nights. Thoropass' Chris Beiro outlines 10 things to consider to ensure your next audit is as stress-free as possible.
Read more

Compliance automation
When Compliance Becomes Theater, Everyone Loses
January 12, 2026
|
Sam Li
Security compliance and audit are at risk of becoming commoditized, where speed and time are the only considerations. What risks does this pose and how can they be avoided?
Read more

SOC 2
Has SOC 2 been commoditized? How to ensure your SOC 2 report helps you strengthen your posture and improve your commercial prospects
December 29, 2025
|
Has SOC 2 been commoditized? It depends. Here's how to ensure your SOC 2 report actually helps you strengthen your security posture.
Read more

ISO 42001
Responsible AI usage: where to begin for security leaders
November 18, 2025
|
Thoropass Team
Getting a handle on AI usage in your organization can be challenging. Learn more about how to get started.
Read more
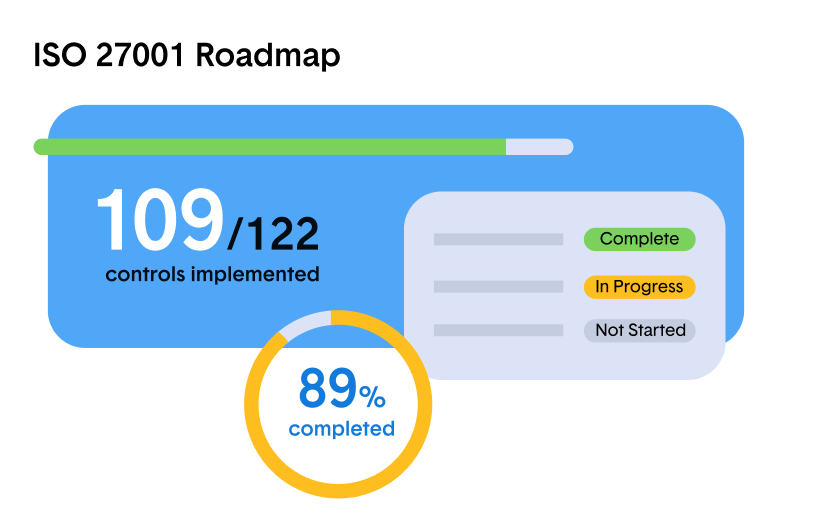
News and Events
Thoropass recognized by Frost & Sullivan for customer value leadership
September 30, 2025
|
Thoropass Team
Read more

Audit
How Sinch modernized their audit process with Thoropass
September 23, 2025
|
Thoropass Team
We spoke with Dan Ross, Sinch's Director GRC, to learn more about how they improved their audit process and reduced team frustration.
Read more

Compliance
Reducing risk and increasing ROI: why new industries are increasingly turning to HITRUST for certification
September 19, 2025
|
Thoropass Team
Read more

Curated by experts
We provide the compliance expertise, so you don’t have to
At Thoropass, we’re more than a readiness solution. Our team of experts are equipped with insight and hands-on experience to provide you with industry-leading perspective and guidance.
Meet the Experts
Stay connected
Subscribe to receive new blog articles and updates from Thoropass in your inbox.
Oops! Something went wrong while submitting the form.
Want to join our team?
Help Thoropass ensure that compliance never gets in the way of innovation.
View open roles












.png)