For enterprises managing complex technology stacks and sensitive data, SOC 2 audits have become a critical yet increasingly burdensome aspect of maintaining customer trust and market access. The traditional approach to SOC 2 compliance—treating it as an annual checkbox exercise—is creating significant operational strain on organizations, with compliance teams spending countless hours manually collecting evidence, coordinating across departments, and managing multiple audit cycles.
The reality is that enterprise organizations are outgrowing conventional SOC 2 audit processes. As technology environments become more complex and customer security expectations rise, the limitations of point-in-time assessments and siloed compliance workflows become increasingly apparent. Compliance leaders find themselves caught in a cycle of reactive documentation, redundant evidence collection, and unpredictable audit timelines—all while trying to maintain continuous security assurance for customers and stakeholders.
However, forward-thinking organizations recognize that SOC 2 compliance doesn’t have to be this way. By transforming SOC 2 from a periodic hurdle into an opportunity for continuous compliance, enterprises can streamline their audit processes and create lasting operational advantages. This shift involves reimagining how controls are monitored, evidence is collected, and compliance is maintained across multiple frameworks—ultimately turning what was once a resource drain into a strategic asset for building customer trust and accessing new markets.
Key takeaways
- Traditional point-in-time SOC 2 audits are no longer sufficient for modern enterprises. By shifting to continuous compliance monitoring, organizations can transform their SOC 2 program from a periodic burden into a strategic advantage that builds customer trust and accelerates market access.
- Today’s complex regulatory landscape demands a more intelligent approach to compliance. Through automated evidence collection and framework integration, enterprises can dramatically reduce the complexity and cost of SOC 2 audits while maintaining rigorous security standards.
- The future of SOC 2 audits lies in the convergence of modern technology and expert guidance. By leveraging compliance platforms built with direct auditor input, organizations can ensure their continuous compliance efforts translate directly into streamlined audits—eliminating surprises and creating predictable, efficient assessment cycles.
The enterprise impact of SOC 2
SOC 2 has evolved beyond a simple security attestation into a fundamental market requirement for enterprise organizations. According to IBM & Ponemon Institute research, nearly 30% of businesses will experience a data breach in the next two years. As organizations scale their digital operations and handle increasingly complex customer data, SOC 2 serves as both a framework for robust data security controls and a universal language for demonstrating trustworthiness to stakeholders.
The business impact of SOC 2 extends far beyond compliance checkboxes. A strong SOC 2 program streamlines enterprise sales cycles by immediately validating security controls and eliminating lengthy security reviews that can delay deal closure.
Furthermore, it simplifies vendor risk assessments and enables faster market access—particularly crucial for enterprises navigating complex supply chains, business partners, or operating in regulated industries. Organizations without a current SOC 2 report often find themselves excluded from vendor selection processes or facing extensive security questionnaires that drain resources and delay revenue recognition.
Six common SOC 2 audit challenges for enterprise organizations
Enterprise organizations face several distinct challenges when managing SOC 2 audits, particularly as compliance requirements grow more complex and interconnected. Here’s an examination of the key obstacles that often impede efficient SOC 2 compliance programs.
1. Framework overlap and audit fatigue
Enterprises rarely pursue SOC 2 in isolation. The challenge isn’t simply managing multiple frameworks simultaneously—it’s the repetitive nature of evidence collection and documentation across these frameworks.
Organizations may find themselves in a perpetual audit cycle, gathering identical evidence multiple times as they move from SOC 2 to ISO 27001 to HIPAA, etc. This redundancy creates significant operational inefficiency and team burnout, particularly when using traditional, siloed compliance management approaches.
2. Resource drain
Manual evidence collection remains one of the most resource-intensive aspects of SOC 2 audits. Without automation, organizations typically dedicate multiple full-time employees solely to evidence collection and management.
Enterprise compliance teams often spend countless hours tracking down screenshots, configurations, and policy documents across various systems and departments. This manual approach not only consumes valuable time but also increases the risk of human error and inconsistencies in documentation.
3. Operational disruption
The impact of SOC 2 audits extends far beyond the compliance team. Multiple audit cycles throughout the year create significant disruption across engineering, IT, and security teams, who must repeatedly pause their core responsibilities to assist with evidence collection and control validation.
This stop-start pattern of audit preparation and response can severely impact project timelines and innovation initiatives, creating a hidden cost to business agility.
4. Cost unpredictability
While organizations typically budget for direct audit costs, the actual expense of SOC 2 compliance often exceeds initial estimates. Hidden costs emerge from unexpected scope expansions, additional evidence requests, and the need for remediation work.
Enterprise organizations frequently find themselves allocating additional resources mid-audit to address gaps or expanding audit scope to meet evolving customer requirements, making it difficult to predict and manage compliance budgets effectively.
5. Stakeholder management
Coordinating SOC 2 audit activities across large, complex organizations presents a significant challenge.
Compliance teams must orchestrate evidence collection and reviews across multiple departments, align with auditor timelines, and maintain clear communication with leadership about audit progress and findings. This complex web of stakeholders often leads to bottlenecks, miscommunication, and delayed audit completion.
6. Compliance sustainability
Point-in-time assessments no longer meet the demands of modern enterprise security requirements. Organizations struggle to maintain continuous compliance between audit cycles, often discovering control gaps or documentation issues only during the next audit period.
This reactive approach creates unnecessary risk exposure and increases the likelihood of audit findings, making it challenging to maintain a consistent security posture throughout the year.

RECOMMENDED READING
Auditing the auditors: 6 steps to performing diligence on your biggest investment
Why traditional SOC 2 audit approaches fall short
Traditional approaches to SOC 2 audits, largely built around manual processes and disconnected systems, are increasingly misaligned with the needs of modern enterprise organizations. Understanding these limitations is crucial for organizations looking to modernize their compliance programs.
The spreadsheet trap
The reliance on spreadsheets for tracking SOC 2 compliance creates significant operational inefficiencies and control gaps.
Enterprise organizations managing hundreds of controls across multiple frameworks quickly become overwhelmed by version control issues, broken formulas, and incomplete audit trails.
This manual approach increases the risk of oversight and makes it impossible to maintain real-time visibility into compliance status—a critical requirement for organizations operating in dynamic technology environments.
Framework silos
Traditional compliance management approaches treat each framework as separate entities, creating unnecessary duplication of effort and resource waste.
When SOC 2, ISO 27001, and other frameworks are managed in isolation, organizations fail to leverage the natural overlap between control requirements. This siloed approach increases the workload on compliance teams. Moreover, it creates inconsistencies in how controls are implemented and documented across different frameworks.
Audit redundancy
The inability to efficiently reuse evidence across multiple frameworks forces organizations into a cycle of repetitive documentation. Compliance teams find themselves collecting the same system configurations, policy documents, and control evidence multiple times throughout the year for different audits. This redundancy wastes valuable time and increases the likelihood of inconsistencies in how controls are documented and demonstrated across different assessments.
Limited visibility
Poor transparency between organizations and auditors creates unnecessary friction and delays in the audit process. Without real-time collaboration tools and clear visibility into audit progress, organizations often discover documentation gaps or control deficiencies late in the audit cycle. This reactive approach leads to rushed remediation efforts, extended audit timelines, and increased costs—all of which could be avoided with better communication and transparency throughout the audit process.
Modernizing your SOC 2 audit process for continuous compliance
Transforming SOC 2 audits into a continuous compliance program requires a strategic shift in both technology and methodology. Modern enterprises are discovering that the right combination of automation, integration, and collaboration can fundamentally change how they approach compliance.
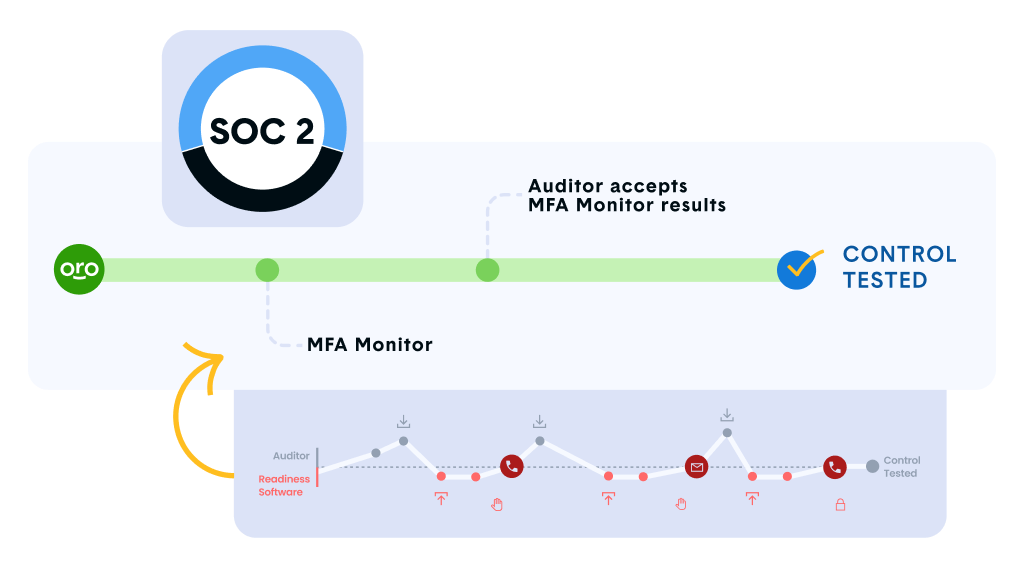
Continuous control monitoring
Moving beyond periodic assessments: Modern compliance platforms enable real-time visibility into control effectiveness. Organizations can monitor their security posture continuously through automated control validation, receiving immediate alerts when configurations drift from approved baselines.
This proactive approach, supported by platforms like Thoropass, allows compliance teams to identify and address issues before they become audit findings, significantly reducing the risk of non-compliance between assessment periods.
Automated evidence collection
Manual evidence-gathering becomes unsustainable as organizations scale their compliance programs. Automated evidence collection transforms this process by continuously capturing and organizing compliance artifacts from across the technology stack.
By establishing automated connections to critical systems and infrastructure, enterprises can maintain an always-current repository of evidence, eliminating the mad dash for documentation during audit periods and ensuring consistency in how controls are demonstrated.
Cross-framework mapping
Modern compliance platforms leverage the natural overlap between security frameworks to maximize efficiency. Through intelligent control mapping, organizations can automatically map a single piece of evidence across multiple frameworks—from SOC 2 to ISO 27001 to HIPAA.
This approach eliminates the redundant evidence collection that plagues traditional compliance programs, allowing enterprises to streamline their audit processes while maintaining rigorous standards across all frameworks.
Unified compliance platform
A centralized compliance platform serves as the single source of truth for all audit-related activities.
Organizations gain unprecedented visibility into their compliance program by consolidating control documentation, evidence collection, and stakeholder communication in one platform. This unified approach eliminates the version control issues and communication gaps that often arise from managing compliance through disconnected spreadsheets and email chains.
Auditor collaboration
Modern compliance platforms transform the traditionally adversarial audit process into a collaborative partnership. Real-time sharing capabilities and structured workflows enable transparent communication between organizations and auditors throughout the assessment cycle. This level of collaboration helps identify and address potential issues early, reducing audit timelines and eliminating the surprise findings that often lead to scope creep and increased costs.
The Thoropass advantage for SOC 2 audits
Transform your SOC 2 audit experience with a platform designed specifically for enterprise compliance needs. Here’s how Thoropass delivers measurable advantages for organizations seeking to modernize their compliance programs:
- Purpose-built platform: Unlike generic compliance tools, Thoropass was designed with direct input from auditors to address the unique challenges of enterprise SOC 2 audits. Our platform incorporates auditor best practices and requirements directly into its workflows, ensuring that every action you take aligns with audit expectations. This purpose-built approach eliminates the guesswork and surprises that often plague traditional audit processes.
- Multi-framework efficiency: Break free from the constraints of framework silos. Thoropass’s intelligent control mapping automatically connects your SOC 2 controls with other frameworks like ISO 27001, ISO 42001, HITRUST, HIPAA, and more. Evidence collected for one framework automatically satisfies requirements across others, dramatically reducing the time and effort needed to maintain multi-framework compliance. Our single repository approach ensures consistency while eliminating redundant documentation efforts.
- Expert support: Thoropass’s in-house auditors bring deep expertise, extensive experience, and a modern approach to IT audits. Our rigorous standards ensure every report is accurate, reliable, and respected in the marketplace, giving you confidence in your compliance journey. Additionally, Our team provides strategic guidance on control implementation, evidence collection, and audit preparation, ensuring you have the support needed to navigate complex compliance requirements successfully and efficiently.
- Predictable timeline: Replace unpredictable audit cycles with a structured, reliable process. Thoropass’s automated workflows and proactive monitoring capabilities help identify and address potential issues before they impact your audit timeline. Our platform’s built-in project management tools and milestone tracking ensure your audit stays on schedule, enabling better resource planning and reduced operational disruption.
- Cost control: Eliminate the hidden costs and scope creep that plague traditional audit approaches. By automating evidence collection, streamlining stakeholder communication, and maintaining continuous compliance monitoring, Thoropass helps organizations reduce the total cost of their SOC 2 program. Our platform’s efficiency gains typically result in significant reductions in both direct audit costs and internal resource requirements.
Ready to transform your approach to SOC 2 compliance? Schedule a demo today to see how Thoropass can help your organization build a more efficient, predictable, and sustainable compliance program. Our experts will show you how to turn compliance from a periodic challenge into a continuous competitive advantage.
Frequently asked questions
What is a SOC 2 audit?
A SOC 2 audit is a comprehensive evaluation of a service organization’s information security management system and internal controls, designed by the American Institute of Certified Public Accountants (AICPA) to assess the operating effectiveness of an organization’s security protocols. Unlike SOC 1, which focuses on financial reporting controls, SOC 2 specifically examines how well an organization protects customer data against unauthorized access, security incidents, and other vulnerabilities based on the AICPA’s Trust Services Criteria.
The audit can be conducted as either a Type 1 or Type 2 assessment by a certified public accountant (CPA). A Type 1 audit evaluates your security controls at a specific point in time, while a Type 2 audit examines how effectively these controls operate over a period of 3-12 months. The resulting report provides stakeholders with detailed assurance about your organization’s security practices, control environment, and commitment to protecting sensitive information, making it a critical component of vendor risk management programs.
What's the difference between SOC 2 Type 1 and Type 2?
SOC 2 Type 1 and Type 2 reports differ primarily in their scope and assessment period.
- A Type 1 report provides a snapshot assessment of your security controls at a specific point in time, evaluating whether they’re properly designed to meet the Trust Services Criteria. Think of it as a photograph of your security posture on a given date.
- A Type 2 report, considered more comprehensive, examines how effectively your controls operate over an extended period, typically 3-12 months. This report demonstrates not just the design but the ongoing effectiveness of your security program. While Type 1 reports can be useful for organizations just beginning their compliance journey, most enterprise customers require Type 2 reports as they provide stronger assurance of sustained security practices.
Read more about Understanding SOC 2 Type 1 vs Type 2.
How long does a SOC 2 audit take?
The duration of a SOC 2 audit varies depending on several factors, particularly whether you’re pursuing a Type 1 or Type 2 report. For a Type 1 audit, the assessment typically takes 3-4 months from preparation to final report issuance. This includes time for evidence collection, control validation, and report preparation.
Type 2 audits require a longer timeline because they evaluate controls over an extended period. The observation period typically ranges from 3-12 months, with most organizations opting for a 6-12 month window to provide robust assurance to customers. However, with proper preparation and automated compliance tools, organizations can significantly streamline the audit process by maintaining continuous evidence collection and control monitoring throughout the year.
How much does a SOC 2 audit cost?
The cost of a SOC 2 audit varies significantly based on several key factors: your organization’s size and complexity, the scope of systems being assessed, whether you’re pursuing Type 1 or Type 2 attestation, and the maturity of your existing control environment. Enterprise organizations often find that the total cost extends beyond just audit fees to include preparation expenses, technology investments, and internal resource allocation.
When evaluating SOC 2 costs, it’s important to consider the efficiency gains possible through modern compliance approaches. Organizations that leverage automated compliance platforms and pursue integrated audits across multiple frameworks (such as SOC 2 alongside ISO 27001) can significantly reduce their total compliance spend while achieving broader coverage.
For a detailed cost analysis based on your organization’s specific needs and objectives, connect with our compliance experts who can help you develop a strategic approach to optimize your compliance investment.
What are the five Trust Services Criteria?
The Trust Services Criteria (TSC) form the foundation of SOC 2, establishing the key principles against which an organization’s security controls are evaluated. The Security criterion, also known as the Common Criteria, is mandatory for all SOC 2 reports, while organizations can choose to include additional criteria based on their business needs and customer requirements.
The five Trust Services Criteria are:
- Security: Protects systems and data against unauthorized access, focusing on core security principles like access controls, encryption, and incident response
- Availability: Ensures systems are operational and accessible as committed or agreed with customers
- Processing integrity: Validates that system processing is complete, accurate, timely, and authorized
- Confidentiality: Safeguards information designated as confidential through appropriate controls and data handling practices
- Privacy: Addresses the collection, use, retention, disclosure, and disposal of personal information in accordance with privacy commitments and requirements
Who needs SOC 2 compliance?
Any organization that stores, processes, or transmits customer data in the cloud should consider SOC 2 compliance, particularly software-as-a-service organizations (SaaS), cloud service providers, and technology vendors. For enterprise organizations, SOC 2 has become a de facto requirement for conducting business, especially when handling sensitive customer information or operating in regulated industries.
While SOC 2 is technically voluntary, market demands often make it essential for business growth. Enterprise customers typically require their vendors to maintain SOC 2 compliance as part of their third-party risk management programs. Organizations looking to move upmarket, enter regulated industries, or expand their enterprise customer base find that SOC 2 compliance is not just a security initiative but a strategic business enabler that opens doors to new opportunities and partnerships.
How often do you need a SOC 2 audit?
For Type 2 reports, which most enterprise customers require, organizations typically undergo annual SOC 2 audits that examine controls over a 12-month observation period. After the initial report is issued, subsequent annual audits help maintain continuous validation of your security controls and ensure there are no gaps in coverage that could concern customers or stakeholders.
However, modern approaches to compliance are shifting from viewing SOC 2 as an annual event to maintaining continuous compliance throughout the year. Through automated control monitoring and real-time evidence collection, organizations can maintain a constant state of audit readiness while reducing the resource intensity traditionally associated with annual assessments. This approach not only streamlines the formal audit process but also provides stronger assurance to customers who increasingly expect continuous validation of security controls.
How do you prepare for a SOC 2 audit?
Successful SOC 2 audit preparation requires a structured approach that begins well before the actual assessment. Here’s a strategic roadmap for organizations preparing for their SOC 2 audit:
Define your scope and requirements
- Determine which Trust Services Criteria apply to your organization beyond the mandatory Security criterion
- Identify all systems, processes, and data that fall within the audit scope
- Document your service commitments and system requirements
- Define clear objectives and timelines for the audit process
Assess your current environment
- Conduct a gap analysis against the SOC 2 requirements
- Review existing policies and procedures for alignment with Trust Services Criteria
- Evaluate current security controls and their documentation
- Identify areas requiring remediation or enhancement
Establish your control framework
- Develop or update security policies and procedures
- Implement required technical controls across your infrastructure
- Create documentation templates for control evidence
- Establish processes for continuous control monitoring
- Configure automated evidence collection where possible
Prepare your evidence collection strategy
- Create an evidence collection matrix mapping controls to requirements
- Set up a centralized repository for audit documentation
- Implement automated evidence collection tools to streamline the process
- Establish clear ownership for each control and its associated evidence
Conduct internal readiness assessment
- Perform a mock audit to identify potential gaps
- Test control effectiveness and documentation completeness
- Review evidence quality and consistency
- Address any identified issues before the formal audit
Engage with stakeholders
- Brief key team members on their roles and responsibilities
- Establish clear communication channels with your auditor
- Set expectations with leadership regarding timeline and resource requirements
- Prepare teams for potential auditor interviews and system demonstrations
The most efficient approach to SOC 2 preparation leverages automated compliance platforms that can streamline these steps through continuous control monitoring, automated evidence collection, and real-time gap analysis. This not only accelerates audit readiness but also establishes sustainable compliance processes that reduce the burden of future audits.
What does a SOC 2 audit include?
A SOC 2 audit involves a comprehensive evaluation of your organization’s security controls and practices by a certified public accountant (CPA). The audit process examines how effectively your organization implements and maintains controls across several key domains:
System description and infrastructure
- Detailed documentation of your organization’s services, system components, and infrastructure
- Overview of relevant technologies, processes, and personnel
- Description of your data handling practices and security commitments
Control environment assessment
- Review of organizational structure, governance, and systems and organization controls framework
- Evaluation of enterprise-wide risk assessment and management processes
- Analysis of information security policies, procedures, and control implementation
- Assessment of change management protocols and secure system development practices
- Examination of identity and access management controls, including user provisioning and authentication mechanisms
- Validation of continuous monitoring capabilities and incident response procedures
- Documentation of internal controls testing and effectiveness measures
Evidence collection and validation
- Review of control documentation and implementation evidence
- System configuration and security settings verification
- Assessment of control monitoring and testing procedures
- Validation of incident response and recovery processes
- Evaluation of vendor management practices
- Analysis of compliance monitoring and reporting mechanisms
The depth and breadth of the audit depend on which Trust Services Criteria are in scope and whether you’re pursuing a Type 1 or Type 2 report. Modern audit approaches leverage automated compliance platforms to streamline evidence collection and maintain continuous control validation, making the audit process more efficient and less disruptive to business operations.

Related Posts
Stay connected
Subscribe to receive new blog articles and updates from Thoropass in your inbox.
Want to join our team?
Help Thoropass ensure that compliance never gets in the way of innovation.

.webp)













.png)