An ISO 27001 risk assessment is a systematic process used to identify, evaluate, and address information security risks within an organization. ISO 27001 is an international standard for Information Security Management Systems (ISMS), and performing a risk assessment is a fundamental requirement of this standard.
The primary goal of an ISO 27001 risk assessment is to ensure that an organization can identify potential security risks to its information assets and implement appropriate measures to mitigate these risks. This process helps organizations:
- Protect sensitive data
- Ensure business continuity
- Comply with legal and regulatory requirements
Key takeaways
- An effective ISO 27001 risk assessment identifies and addresses potential information security risks, which is essential for maintaining compliance and enhancing overall security within an organization.
- Key components of a robust ISO 27001 risk assessment include a risk management framework, defined risk criteria and acceptance criteria, and a comprehensive inventory of information assets.
- Continuous monitoring and documentation of the risk assessment process, along with effective communication of findings to stakeholders, are vital for ongoing compliance and improving an organization’s information security management system.
Understanding ISO 27001 risk assessments
The ISO 27001 risk assessment process is an essential, systematic approach for recognizing potential risks that could jeopardize information security. It’s a critical component in establishing and maintaining an effective information security management system (ISMS) by thoroughly evaluating all possible areas of vulnerability within the organization’s framework.
Executing a detailed and precise information security risk assessment is required for organizations aiming to attain ISO 27001 certification. By conducting meticulous risk assessments, businesses can identify which protective measures are necessary to defend against risks, potentially simplifying the path to ISO 27001 certification.
Undertaking regular ISO 27001-compliant risk assessments also brings advantages that exceed compliance. Proactively addressing foreseeable dangers with established countermeasures strengthens an organization’s security around informational assets.
Six key steps in ISO 27001 risk assessment
Executing a risk assessment under ISO 27001 encompasses multiple steps, each integral to the overarching risk management strategy. This enables organizations to methodically tackle and lessen the impact of identified risks within their operations.
1. Identify assets and scope
Defining the scope of the Information Security Management System (ISMS) is the first step in the ISO 27001 risk assessment process. This involves determining the boundaries and applicability of the ISMS within the organization. It is essential to clearly outline which parts of the organization will be covered by the ISMS to ensure a focused and effective risk management approach.
Once the scope is defined, the next step is to identify all information assets that need protection. These assets can include data, hardware, software, and even people. Each asset should be documented with relevant details such as its location, owner, and the type of information it handles.
By establishing a clear scope and identifying all critical information assets, organizations can ensure that their risk assessment process is thorough and targeted, providing a strong foundation for effective information security management.
2. Identify risks, threats, and vulnerabilities
The next phase of the risk assessment methodology involves pinpointing potential challenges that may compromise the information security of the assets identified in step one.
As part of the risk management process, it’s important to identify existing threats and weaknesses linked to each piece of an organization’s assets. Subsequently, it’s essential to determine how likely these risks are to occur and their projected impact on information safety.
Moreover, for every risk listed within the risk treatment plan, an appointed individual (a ‘risk owner’) must be accountable for its mitigation and overseeing any remaining residual risk as part of treating those risks. It’s imperative to enforce version control over these documents to ensure their reliability remains intact. This practice aids in accurately monitoring revisions made over time.
Common risks, threats, and vulnerabilities
While risks, threats, and vulnerabilities may differ in nature and in potential severity from business to business, there are some usual suspects among threats, including:
- Cyberattacks
- Malware (e.g., viruses, ransomware, trojans)
- Phishing or spear-phishing attacks
- Denial of Service (DoS) or Distributed Denial of Service (DDoS) attacks
- Man-in-the-middle (MITM) attacks
- SQL injection attacks
- Zero-day vulnerabilities
- Insider threats
- Malicious insiders (e.g., disgruntled employees)
- Accidental data leaks or breaches by employees
- Privilege misuse or abuse of access rights
- Physical threats
- Theft of IT equipment (e.g., laptops, servers)
- Unauthorized physical access to data centers or offices
- Natural disasters (e.g., floods, earthquakes, fires)
Power outages or surges
- Human errors
- Misconfigurations of systems or software
- Accidental deletion or modification of data
- Failure to follow security policies
- Supply chain threats
- Compromised hardware or software from third-party vendors
- Dependency on external service providers
- Supply chain disruptions affecting IT operations
- Network vulnerabilities
- Unsecured wireless networks
- Outdated or unpatched software/hardware
- Weak encryption protocols
- Social engineering attacks
- Pretexting or baiting attacks
- Vishing (voice phishing) or SMS phishing
- Tailgating or impersonation attacks
Threats and vulnerabilities go hand-in-hand: Vulnerabilities allow threats to succeed; the vulnerabilities within your IT infrastructure are exactly what cyber attackers will take advantage of. Vulnerabilities can be weaknesses in software, hardware, or even human factors. Conducting vulnerability scans and assessments will help you pinpoint these weak spots.
Here are some of the kinds of vulnerabilities your organization may experience:
- Software vulnerabilities
- Outdated or unpatched software (e.g., operating systems, applications)
- Insecure code (e.g., coding flaws, weak input validation)
- Unsupported software versions (end-of-life software)
- Weak or default configuration settings (e.g., disabled security features)
- Network vulnerabilities
- Unsecured or misconfigured firewalls
- Lack of network segmentation (e.g., flat network structure)
- Open ports or services that aren’t monitored
- Weak or outdated encryption protocols (e.g., SSL instead of TLS)
- Unsecured Wi-Fi networks or public Wi-Fi use
- Authentication and access control issues
- Weak or reused passwords
- Lack of multi-factor authentication (MFA)
- Poorly managed privileged accounts (e.g., excessive admin rights)
- Inadequate user access controls (e.g., lack of role-based access control)
- Unmonitored user accounts (e.g., orphaned accounts from former employees)
- Data management vulnerabilities
- Unencrypted sensitive data (At rest or in transit)
- Poor data classification and handling policies
- Lack of data loss prevention (DLP) Controls
- Inadequate backup and recovery procedures
- Insecure cloud storage or third-party storage services
- Physical security weaknesses
- Lack of physical access controls (e.g., unlocked server rooms, no surveillance)
- Inadequate protections for portable devices (e.g., laptops, smartphones)
- Poor environmental controls (e.g., temperature, humidity) in data centers
- Lack of secure disposal methods for hardware and documents
- Human factors
- Lack of security awareness training for employees
- Failure to follow security policies or procedures
- Social engineering susceptibility (e.g., phishing, tailgating)
- Poor incident response processes (e.g., delayed or ineffective response)
- Third-party and supply-chain vulnerabilities
- Lack of vetting for third-party vendors and service providers
- Insecure third-party applications or hardware
- Poor contract management regarding security responsibilities
- Inadequate monitoring of third-party activities
- System configuration vulnerabilities
- Insecure default configurations for hardware/software
- Poorly configured security tools (e.g., intrusion detection/prevention systems)
- Lack of logging and monitoring for critical systems
- Weak backup procedures and recovery plans
- Mobile and IoT device vulnerabilities
- Insecure mobile devices (e.g., lack of encryption, no remote wipe capabilities)
- Poor security for Internet of Things (IoT) Devices (e.g., default passwords, weak updates)
- Insecure or unpatched mobile apps
Utilizing workshops with specialists during the risk assessment procedure can help pinpoint such hazards systematically. To achieve a robust evaluation across all aspects following ISO 27001 guidelines, an asset-based strategy is advocated for identifying threats extensively. This strategy lays a solid foundation for effective risk management strategies and actions aimed at mitigating the associated dangers.
3. Using a scoring system: Evaluate risks, threats, and vulnerabilities
As you can see from the above lists, you can end up with a long list of potential risks. So, what’s needed now is some way of prioritizing them. This step does exactly that: Following the identification of risks, analysis, and scoring are the next steps.
This entails determining values for both the impact and probability of each risk by considering elements such as how quickly it could take effect and its chances of occurring. By evaluating the potential that a threat will exploit a vulnerability along with its possible consequences, organizations can establish an order of precedence for tackling risks.
In performing risk assessments, scores ranging from 1 to 10 are typically utilized to gauge both likelihood and impact. These evaluations assist in organizing which risks should be addressed first during risk treatment initiatives. Higher-scoring threats demand more immediate attention.
Risk tolerance and risk acceptance criteria
Involving leadership teams is an important step when deciding on an acceptable level of risk for any organization. This determination must support organizational goals while ensuring prioritization remains in line with strategic objectives.
Each organization’s risk tolerance plays a significant role in shaping its risk assessment and management strategies. Risk tolerance refers to the level of risk an organization is willing to accept in pursuit of its objectives. This tolerance varies widely depending on factors such as industry, regulatory environment, and organizational culture.
By understanding and defining their risk tolerance by articulating ‘risk acceptance criteria’, organizations can more effectively prioritize which risks to mitigate, transfer, accept, or avoid, ensuring that their risk management efforts align with their overall strategic goals.
4. Develop a risk treatment plan
By now, the risks have been identified and prioritized. It’s time to start a treatment plan. The goal of this step is to handle risks adequately and either eliminate them or diminish them to tolerable levels.
The treatment plan specifies the organization’s approach to tackling identified risks by delineating practical measures, implementation schedules, and the resources allocated for risk mitigation.
You might think the only option to treat risks is to ‘fix them’ but there are a few different approaches to handling the identified risks, including:
- Mitigation: This strategy aims at applying measures to decrease the level of risk. For example, an organization may mitigate identified risks by implementing a firewall to protect against cyberattacks.
- Transfer: Through this approach, responsibility for the risk is allocated to a third party, like via insurance policies or by outsourcing tasks. For instance, purchasing cyber insurance to cover the costs associated with data breaches.
- Acceptance: Opting for this means deciding not to take any specific action and accepting the consequences of the risk. For example, a company might accept the risk of minor data loss due to its low impact, especially if it enables faster business growth.
- Avoidance: This entails avoiding actions that would lead to exposure to the particular risk. For example, discontinuing the use of a vulnerable software application to prevent potential security breaches.
Treatment plans can involve implementing new security controls, enhancing existing ones, or accepting certain risks if they are within the organization’s risk tolerance.
Ensuring that clear documentation explains why certain approaches were selected promotes transparency and accountability in the risk treatment process. After evaluating potential threats, an organization prepares a summary report that outlines how it intends to continue management efforts with respect to those recognized as significant.
5. Document the process and assign responsibility
Having taken great steps to identify, prioritize, and discuss treatment plans for risks, it’s important to record the information and decisions.
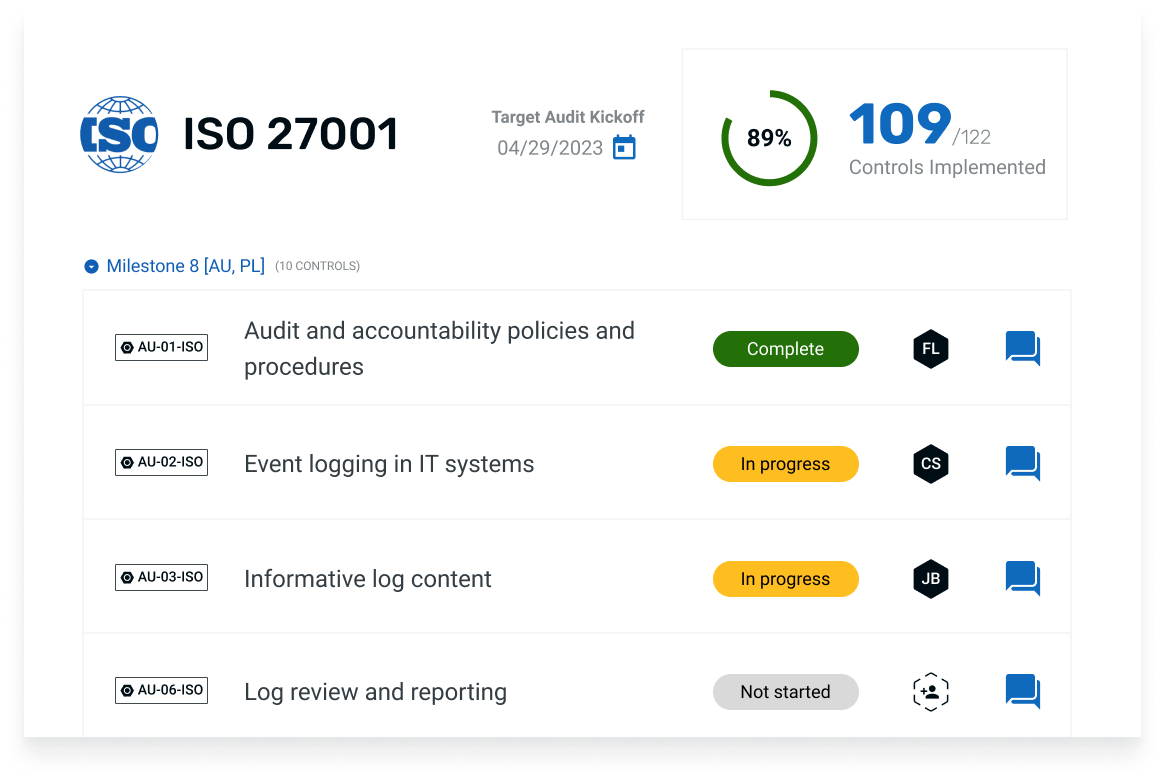
Indeed, the creation of a risk treatment plan document is a key step in detailing the methods for addressing risks, guaranteeing comprehensive coverage throughout execution. This document should incorporate a Statement of Applicability (SoA), which reviews controls and specifies approaches to manage identified risks. By doing so, it promotes more efficient audits and improves ease of reference for internal teams, ultimately improving the management of risk.
Crafting a management summary report that presents these insights effectively promotes comprehension and supports stakeholders in making knowledgeable decisions. This can ensure that all involved parties are aware of the organization’s stance on risk and countermeasures. Correlating the risk assessment outcomes with organizational aims for pertinent and practical responses is important for the leadership team’s understanding of the decision-making.
Key documents for ISO 27001 risk assessment
- Risk assessment methodology: This document outlines the approach and criteria used for the risk assessment, including how risks are identified, evaluated, and prioritized. It defines the risk assessment scope, the risk criteria (such as impact and likelihood), and the methods used to assess and treat risks.
- Risk assessment report: This comprehensive report details the results of the risk assessment, including the identified risks, their evaluations, and the proposed treatment plans. It often includes:
- A summary of the risk assessment process
- A list of identified assets, threats, and vulnerabilities
- An evaluation of the potential impact and likelihood of each risk
- A risk matrix or register showing the risk levels assigned to each identified risk
- Risk treatment plan: This plan outlines how the organization intends to treat each identified risk. It includes the chosen risk treatment options (e.g., mitigation, transfer, acceptance, or avoidance), the specific controls to be implemented, responsible parties, and timelines for implementation. The plan should align with the organization’s overall risk management strategy and objectives.
- Statement of Applicability (SoA): The SoA is a key document that lists all the ISO 27001 Annex A controls and indicates which controls are applicable or not applicable to the organization. For each control, the SoA provides:
- The justification for inclusion or exclusion
- The status of the implementation
- A reference to where the control is implemented in the organization’s ISMS
- Risk register: A risk register is a dynamic document that logs all identified risks and their details, including the risk description, assessment results, and treatment status. It serves as a central record for monitoring and reviewing risks over time.
- Asset inventory: While not always part of the risk assessment documentation itself, an asset inventory is essential for identifying what needs to be protected. It lists all information assets, including their owners, value, and importance to the organization.
- Control implementation records: Documentation showing the implementation of selected controls, such as technical configurations, policy documents, or evidence of staff training. These records provide proof that the organization has taken steps to mitigate the identified risks.
- Review and monitoring records: Evidence of the ongoing monitoring and review process, including regular risk assessment reviews, internal audits, and management reviews. This documentation demonstrates the organization’s commitment to maintaining and improving its ISMS.
6. Monitor and review
In compliance, nothing is ever really one-and-done: Due to the potential emergence of new risks concurrent with changes in operations, ongoing vigilance in ISO 27001 risk assessments is required.
Periodic updates and evaluations of the risk treatment plan are essential for detecting newly arising risks. Here are some of the steps in monitoring and reviewing your risk assessment:
- Repeat the risk assessment process: It’s recommended that formalized ISO 27001 risk assessments be undertaken annually to confirm their continuous adequacy.
- Internal audits: Utilizing internal audits is a strategy for assessing how well the Information Security Management System (ISMS) functions. Allocating specific responsibilities to risk owners and clearly defined remediation processes is vital for maintaining surveillance over information security management.
- Active risk monitoring: To maintain adherence, automated notifications are triggered and sent directly to designated risk owners whenever there’s a departure from established norms or procedures related to managing identified risks.
Maintaining a risk register
Incorporating a risk register into the risk management process helps effectively track both the actions taken to manage identified risks and any remaining residual risks. This pivotal instrument allows organizations to keep a comprehensive, constantly refreshed log of all recognized potential threats, along with their present status and mitigation efforts. It’s important to consistently revise this register so that it accurately mirrors the evolving nature of information security hazards, allowing for immediate reaction to any shifts in threat severity.
Maintaining an up-to-date risk register serves not just to oversee existing dangers but also to spot emerging new threats. Through meticulous documentation within these records, organizations are enabled to persistently monitor and address every conceivable risk scenario. Such diligent oversight contributes substantially towards enhancing the resilience and reliability of their information security management system.
How compliance software can streamline your ISO 27001 risk assessment
Optimizing the process of risk assessment for ISO 27001 can lead to both time and resource conservation while still maintaining a rigorous and efficient approach to managing risks. Compliance automation can help by:
- Employing templates for risk assessments
- Automating manual tasks
- Enlisting the aid of professionals with experience
By investing in such a tool, organizations can execute comprehensive yet expedient risk assessments. This not only boosts their capability in handling information security threats but also strengthens their overall stance on mitigating risks within the scope of ISO 27001 requirements.
Utilizing risk assessment templates
Utilizing templates can streamline the risk assessment process by offering a predefined format for documentation. These ready-to-use documents enable organizations to maintain uniformity and thoroughness throughout their risk evaluations. Templates equip companies with preset policies and an organized guide, facilitating the initiation of control management while conserving time and minimizing the probability of missing important details.
Thoropass provides a suite of customizable templates tailored to ISO 27001 standards, ensuring that organizations can quickly and efficiently document their risk assessments. By leveraging Thoropass’s comprehensive templates, businesses can maintain consistency and thoroughness, reducing the likelihood of overlooking critical security weaknesses.
Leveraging automation to save time and resources
The implementation of automation tools can markedly decrease the duration needed to perform risk assessments in accordance with ISO 27001 standards. These utilities optimize the compliance procedure, encompassing evidence gathering and task coordination, thereby enhancing the efficacy of appraisals. By automating monotonous duties, organizations can concentrate on more important parts of the risk assessment process.
Thoropass offers advanced AI-enhanced automation tools that streamline the entire risk assessment process. These tools help in automating repetitive tasks, such as evidence collection and task tracking, allowing organizations to focus on critical aspects of their ISO 27001 compliance efforts. With real-time updates and notifications, Thoropass ensures that businesses can effectively manage their risk oversight activities.
Engaging experienced professionals
Involving experts with substantial experience in the risk assessment process is essential for obtaining dependable outcomes. Their specialized knowledge contributes to the precision and efficacy of evaluating risks, guaranteeing that all potential threats are duly recognized and managed. The synergy from interdisciplinary teams fosters an expansive grasp of risk factors and unifies mitigation tactics.
Thoropass connects organizations with experienced professionals who have deep expertise in ISO 27001 compliance. These experts provide tailored guidance and support, ensuring that all potential risks are identified and addressed effectively. By leveraging Thoropass’s professional services, businesses can navigate the complexities of ISO 27001 risk assessments with confidence and efficiency, expediting their path to certification.
Conclusion: Risk requires ongoing vigilance and dialogue
To effectively carry out an ISO 27001 risk assessment, you need to follow a systematic sequence of actions. These range from grasping the fundamental elements necessary for conducting the assessment to formulating and documenting an exhaustive plan for risk treatment.
Utilizing templates, automation technology, and seasoned experts can simplify the information security risk management process and bolster your organization’s protection against information security threats. It’s critical to remember that ongoing vigilance and dialogue are indispensable in maintaining these risk assessment standards while promoting a culture of compliance.
More FAQs
What is the purpose of an ISO 27001 risk assessment?
The purpose of an ISO 27001 risk assessment is to identify potential information security risks and develop strategies to mitigate them, ensuring compliance and enhancing overall security.
What are the key components of an ISO 27001 risk assessment?
The key components of an ISO 27001 risk assessment are a risk management framework, clearly defined risk and acceptance criteria, and the identification of information assets. These elements are essential to effectively assess and manage risks within an organization.
How often should an ISO 27001 risk assessment be conducted?
An ISO 27001 risk assessment should be conducted at least annually to maintain effective risk management and ensure compliance. Regular evaluations help adapt to changing environmental risks.
What are the primary options for responding to identified risks?
Each identified risk can be addressed through various strategies such as mitigation, transfer, acceptance, or avoidance. The choice of strategy should be customized based on the particular aspects of each risk.
How can organizations streamline the ISO 27001 risk assessment process?
Organizations can streamline the ISO 27001 risk assessment process by utilizing risk assessment templates, employing automation tools, and engaging experienced professionals. These strategies enhance efficiency and ensure a thorough evaluation of risks.
Get Started with ISO 27001
Learn how Thoropass can help you get (and stay) compliant
Thoropass supports your success with a clear ISMS readiness roadmap, compliance automations, audit management, and experts to guide your certification journey.
Related Posts
Stay connected
Subscribe to receive new blog articles and updates from Thoropass in your inbox.
Want to join our team?
Help Thoropass ensure that compliance never gets in the way of innovation.
















.png)