For mid-size enterprises, cybersecurity risk management has evolved beyond a simple compliance checkbox into a strategic business imperative. As threats grow more sophisticated and regulatory requirements multiply, large organizations find themselves at a critical juncture: continue with fragmented, reactive approaches or implement an integrated risk management strategy that aligns with business objectives.
The reality is stark: With data breach costs hitting record highs of $4.88 million in 2024 and breaches remaining undetected for an average of 194 days (IBM), enterprises can no longer afford to treat cybersecurity risk management as an isolated IT function. Today’s enterprise security leaders need comprehensive approaches to managing risk that streamline compliance processes, reduce audit fatigue, and transform security from a cost center into a business enabler.
Key takeaways
- Effective cybersecurity risk management must align with business objectives and integrate across departments rather than operating in isolation
- Beyond direct breach expenses, inefficient risk management creates significant operational drag through audit loops, siloed operations, and compliance burnout
- Integrated risk management solutions create a single source of truth for compliance evidence, significantly reducing the total cost of compliance while enabling continuous monitoring
- Organizations facing multiple compliance requirements can streamline efforts through unified evidence collection and cross-framework control mapping
The evolving nature of cybersecurity risk in complex environments
Enterprise cybersecurity risks present fundamentally different challenges compared to those faced by small and medium-sized businesses. While SMBs typically manage limited IT environments with concentrated decision-making and fewer compliance obligations, enterprises contend with sprawling digital ecosystems, complex organizational structures, and multi-jurisdictional regulatory requirements.
This scale difference isn’t merely quantitative—it creates qualitatively different risk profiles that demand more sophisticated management approaches. Enterprise security teams must navigate extensive legacy systems alongside cutting-edge technologies while coordinating security policies across departments with competing priorities and varying levels of security maturity.
The attack surface for large organizations continues to expand at an unprecedented rate. Enterprise environments now encompass thousands of endpoints, cloud resources, Internet of Things (IoT) devices, and third-party connections, all of which create potential vulnerability points.
The consequences of this expanded attack surface are reflected in breach statistics: The average time to identify a breach stands at 194 days (IBM), with an overall breach lifecycle extending to 292 days—a particularly alarming statistic for organizations with extensive digital footprints where undetected threats can propagate across interconnected systems.
In 2025, enterprises face sophisticated threat vectors specifically targeting their unique vulnerabilities. Advanced persistent threats (APTs) increasingly focus on large organizations’ intellectual property and sensitive customer data, while AI-powered attacks can bypass traditional detection measures by mimicking normal network behavior. Supply chain compromises have evolved from theoretical concerns to practical realities, with attackers exploiting the implicit trust between enterprises and their technology vendors.
Compounding these challenges is the ever-expanding regulatory landscape—from industry-specific frameworks like HIPAA and PCI DSS to regional regulations like GDPR and CCPA—creating a compliance matrix that demands integrated risk management approaches. For enterprises operating across multiple jurisdictions, each new regulation doesn’t simply add linear complexity but multiplies compliance challenges exponentially, requiring sophisticated control mapping and evidence management to avoid redundant effort.
The true cost of inadequate cyber risk management
The financial impact of cybersecurity breaches often dominates headlines, with the average cost reaching $4.88 million in 2024. However, for enterprises, inadequate risk management creates cascading costs that extend far beyond direct breach expenses. These hidden costs manifest in operational inefficiencies that can severely impact an organization’s ability to execute business objectives and maintain competitive advantages.
When enterprises rely on fragmented, reactive approaches to risk management, they inevitably enter what security professionals call “audit loops”—repetitive cycles of remediation efforts that consume significant resources without delivering lasting improvements. These loops typically begin when point-in-time assessments reveal gaps that require urgent attention, pulling key personnel away from strategic initiatives to address immediate compliance concerns. Once remediated, these gaps often reappear in subsequent audits because the underlying systemic issues remain unaddressed, creating a perpetual cycle of reactive firefighting.
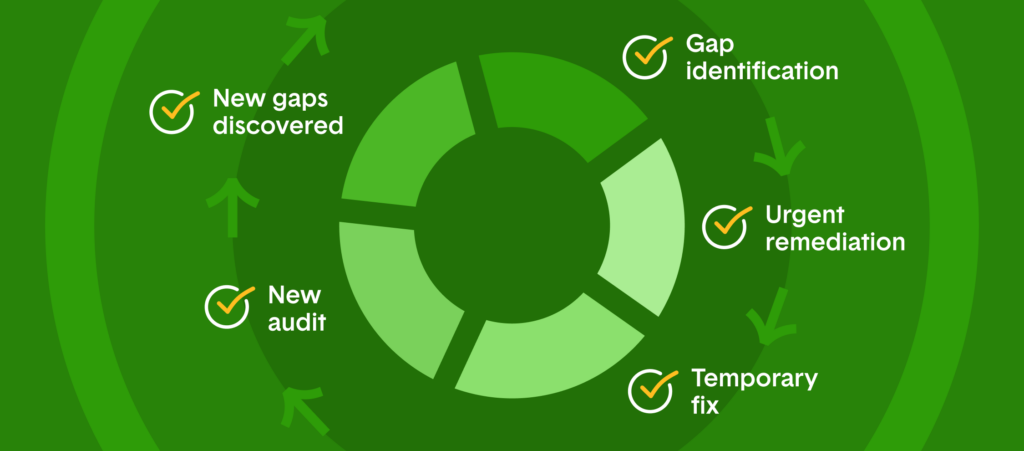
The manual tracking processes that characterize many enterprise compliance programs further compound these inefficiencies. Security and compliance teams often spend disproportionate amounts of time hunting for evidence, updating spreadsheets, coordinating email trails, and preparing documentation—tasks that provide minimal security value while consuming valuable technical resources. These administrative burdens prevent compliance professionals from focusing on strategic risk management activities that could meaningfully improve security posture and add business value.
Perhaps most concerning is how these inefficiencies impact enterprise agility and innovation. Organizations caught in perpetual audit cycles develop risk-averse cultures where innovation takes a backseat to compliance concerns. Security teams become bottlenecks rather than enablers, slowing down technology adoption and business transformation initiatives. In competitive markets where speed often determines success, enterprises burdened with inefficient risk management processes find themselves at a significant disadvantage, unable to pivot quickly or capitalize on emerging opportunities because compliance considerations create friction at every turn.

On-Demand Webinar
Hacking the Modern Audit
Tune in to an hour of critical thinking and discussion about improving audit quality and reducing cost to this critical process.
Five key challenges in enterprise cybersecurity risk management
Enterprise organizations face distinct obstacles when implementing effective cyber risk management programs, often stemming from organizational complexity and scale.
1. Fragmented responsibility across departments
Security and compliance responsibilities frequently span multiple departments with misaligned priorities and communication gaps. IT teams implement controls, legal departments interpret regulatory requirements, business units own specific applications, and compliance teams coordinate audit responses—often with limited visibility into each other’s activities.
This fragmentation creates significant blind spots in the risk landscape. Without clear ownership and coordination mechanisms, critical vulnerabilities can remain unaddressed while duplicate efforts waste resources. Organizations struggle to maintain a unified view of their risk profile when responsibility is distributed without corresponding accountability structures.
2. Audit fatigue and compliance burnout
The proliferation of frameworks and regulations has created a state of perpetual audit readiness that exhausts even well-resourced teams. Many enterprises face multiple overlapping audits annually—from SOC 2 and ISO 27001 to industry-specific regulations like HIPAA or PCI DSS.
This constant pressure leads to compliance burnout, where teams focus narrowly on passing the next audit rather than addressing systemic security issues. The resulting checkbox mentality prioritizes short-term documentation over lasting security improvements, creating a dangerous illusion of protection while fundamental vulnerabilities persist.
3. Integration challenges with legacy systems
Enterprises typically operate complex technology ecosystems that include legacy systems never designed with modern compliance requirements in mind. These systems often lack robust logging capabilities, modern authentication mechanisms, or appropriate security controls.
Integrating these legacy systems into comprehensive risk management programs presents significant technical challenges. Organizations must balance the business value these systems provide against their security limitations, often developing complex compensating controls that require ongoing maintenance and documentation—further stretching already limited security resources.
4. Scaling security with business growth
As enterprises grow through expansion or acquisition, security teams struggle to scale risk management practices accordingly. New business units, geographic regions, or technology stacks introduce unforeseen vulnerabilities and compliance obligations that can quickly overwhelm existing processes.
The security function often lags behind business growth, creating windows of exposure during critical expansion periods. Without scalable, repeatable approaches to risk assessment and management, enterprises find themselves constantly playing catch-up, addressing security as an afterthought rather than integrating it into growth strategies from the outset.
5. The resource drain of manual processes and documentation
Manual evidence collection and documentation processes create an enormous administrative burden that diverts resources from strategic security initiatives. Teams spend countless hours taking screenshots, updating spreadsheets, collecting attestations, and formatting reports to satisfy audit requirements.
This inefficiency is particularly problematic given that human factors remain the primary vulnerability point, with Stanford research indicating that 88 percent of cybersecurity breaches stem from human error. When technical teams are consumed with administrative tasks rather than focusing on security awareness and training, organizations leave their most significant vulnerability—their people—inadequately addressed.
The strategic value of purpose-built risk management platforms
Modern enterprises need integrated risk management approaches that break down silos and create operational efficiencies. Thoropass delivers exactly this through its purpose-built platform designed specifically for enterprise compliance and security needs.
Unifying compliance and security operations
The traditional division between security and compliance teams creates significant inefficiencies in enterprise environments. Thoropass bridges this gap through a unified platform that serves both functions, enabling security findings to automatically feed into compliance documentation and compliance requirements to inform security priorities.
With Thoropass’ Risk Register, organizations gain a 360-degree view of their risk landscape within the same environment they manage compliance readiness and audit processes. This workflow eliminates the common disconnect where security teams identify risks that compliance teams then separately document—often with inconsistent information or duplicate effort. Instead, identified risks are directly linked to controls for treatment, ensuring alignment between security priorities and compliance requirements.
Implementing continuous control monitoring rather than point-in-time assessments
Point-in-time assessments create a false sense of security while allowing risks to develop between assessment periods. Thoropass overcomes this limitation through continuous monitoring capabilities that provide real-time visibility into compliance status and control effectiveness.

The platform’s interactive interface displays compliance status and risk evolution over time, helping security leaders make more informed decisions about their business. This approach transforms compliance from a periodic scramble into an ongoing program with consistent visibility—significantly reducing the risk of control failures between formal audits. For enterprises with complex environments, this continuous visibility is essential for maintaining an accurate understanding of risk posture amid constant change.
Leveraging automation for evidence collection and documentation
Enterprise compliance teams often spend countless hours on manual evidence collection—taking screenshots, formatting documents, and chasing attestations. Thoropass’ platform automates these processes, allowing security professionals to focus on strategic initiatives rather than administrative tasks.
By automating evidence collection and documentation workflows, Thoropass addresses one of the most significant pain points in enterprise compliance: manual overhead. This automation is particularly valuable given that human factors remain the primary vulnerability point.
Establishing multi-framework compliance strategies
Mid-market organizations typically face multiple compliance obligations—from SOC 2 and ISO 27001 to industry-specific regulations like HIPAA and PCI DSS. Thoropass’ platform is specifically designed to support multi-framework requirements through unified evidence collection and cross-framework control mapping.
The platform enables teams to upload evidence once and apply it to multiple frameworks, eliminating the redundant work that plagues traditional compliance approaches. This capability is particularly valuable for enterprises operating across jurisdictions or industries with varied compliance requirements. By leveraging Thoropass’ multi-framework capabilities, organizations can achieve multiple certifications with a single audit process, significantly reducing the resource drain of compliance activities.
Building transparency between compliance teams and auditors
Traditional audit processes often involve lengthy back-and-forth communications, unclear expectations, and unexpected findings. Thoropass transforms this experience by creating unprecedented transparency between compliance teams and auditors.
The platform provides a shared environment where both parties can collaborate efficiently, track progress, and maintain clear communication throughout the audit process. This transparency eliminates the “black box” nature of traditional audits, where compliance teams submit evidence with limited visibility into auditor expectations or assessment progress.
Even with the most sophisticated compliance automation tools, there’s still a missing link when it comes to actual audit execution. That disconnect between the “compliance world” and “audit world” creates confusion, duplicate work, and last-minute scrambles.An integrated approach is the new standard for competitive, security-minded organizations.
For companies managing complex compliance programs, this improved collaboration with auditors reduces uncertainty, accelerates audit timelines, and helps prevent the dreaded “audit loops” that consume significant resources without delivering corresponding value.
Implementation roadmap for mature enterprises
Implementing a strategic cyber risk management process requires a methodical approach, especially for mature enterprises with established processes. Follow this streamlined roadmap:
- Assessing current risk management maturity: Conduct a comprehensive gap analysis against your primary frameworks, examining existing processes, documentation quality, and resource consumption to establish your baseline maturity level.
- Prioritizing improvements based on risk exposure: Focus first on addressing high-impact, high-likelihood risks while targeting inefficiencies that consume disproportionate resources for limited security value.
- Building internal stakeholder alignment: Establish a cross-functional steering committee with clear ownership for compliance and risk management responsibilities, ensuring security and compliance teams operate with shared objectives.
- Selecting the right technology partners (and auditor): Choose a purpose-built platform like Thoropass that supports your specific compliance frameworks with automation capabilities and continuous monitoring to streamline audit processes.
- Measuring success beyond compliance checkboxes: Track reductions in total compliance effort, time-to-certification, and audit findings while evaluating how compliance activities contribute to overall security posture improvement.
Conclusion: From compliance burden to strategic advantage
Cybersecurity risk management has evolved from a necessary evil into a strategic differentiator for forward-thinking enterprises. Organizations that transform their approach gain measurable competitive advantages—faster product launches, more efficient operations, and greater market agility—while simultaneously strengthening their security posture against evolving threats.
As regulatory requirements multiply, enterprises with integrated risk management approaches maintain resilience through continuous monitoring and automated evidence collection rather than constantly rebuilding compliance programs. Thoropass offers exactly this: a purpose-built platform designed for enterprise risk management needs that eliminates spreadsheets, endless email chains, and unpredictable audit cycles.
Book a demo today to discover how Thoropass can help your organization build a more efficient, effective approach to managing cybersecurity risk while reducing the total cost of compliance.
Frequently asked questions
What is cybersecurity risk management?
Cybersecurity risk management is the structured process of identifying, assessing, and mitigating risks to an organization’s digital assets, operations, and sensitive information. It involves systematically analyzing potential threats and vulnerabilities within your IT environment, evaluating their potential impact, and implementing appropriate controls to address them.
Why is cybersecurity risk management important for businesses?
Cybersecurity risk management is crucial because it enables businesses to protect critical assets while efficiently allocating limited security resources. With the average data breach costing $4.88 million in 2024 and breaches remaining undetected for an average of 194 days (IBM), organizations face significant financial, operational, and reputational consequences from inadequate security.
Beyond direct breach costs, effective risk management prevents disruptions to business operations, maintains customer trust, and ensures regulatory compliance across multiple frameworks.
What are the four steps of cybersecurity risk management process?
The cybersecurity risk management process consists of four essential steps that form a continuous cycle:
Identify: Catalog all digital assets, including data, systems, and third-party connections. Document potential risks and threats to these assets and identify vulnerabilities that could be exploited.
Assess: Evaluate identified risks by analyzing both the likelihood of exploitation and the potential impact if a breach occurs.
Mitigate: Implement appropriate controls to address prioritized risks. This may include technical solutions (encryption, access controls), procedural changes (new policies), or transferring risk through insurance. Not all risks will be eliminated—some may be accepted if the cost of mitigation exceeds potential impact.
Monitor: Continuously track the effectiveness of implemented controls and watch for emerging threats or changing risk profiles. This ongoing observation ensures the risk management program remains relevant as the threat landscape and business environment evolve.
How do you develop a cybersecurity risk management plan?
Developing an effective cyber risk management initiative starts with establishing clear objectives aligned with your business goals and compliance requirements. Begin by conducting a comprehensive asset inventory, identifying what you need to protect and its relative importance to operations. Next, assess your current security posture through vulnerability scanning, penetration testing, and control evaluations to identify gaps.
Create a risk register that documents identified risks, their potential impact, and likelihood of occurrence, then prioritize them based on criticality. Develop mitigation strategies for priority risks, including specific controls, responsible parties, timelines, and success metrics. Establish a continuous monitoring program with clear processes for reassessing risks and evaluating control effectiveness.
Finally, ensure your plan includes specific procedures for incident response, escalation paths, and business continuity to maintain operations during security events. The most effective plans incorporate stakeholders from across the organization—including IT, legal, operations, and executive leadership—to ensure comprehensive risk visibility and organizational alignment.
What frameworks are used for cybersecurity risk management?
Several established cybersecurity risk management frameworks provide structured approaches, each with different strengths and focus areas. The NIST Cybersecurity Framework (CSF) offers a comprehensive, accessible approach with five functions: Identify, Protect, Detect, Respond, and Recover. For organizations requiring more detailed guidance, the NIST Risk Management Framework (RMF) provides a seven-step process for integrating security into the system development lifecycle.
ISO 27001 presents an internationally recognized framework for implementing an Information Security Management System (ISMS), with explicit risk assessment requirements. The CIS Controls offer a prioritized set of security actions organized into implementation groups based on organizational maturity.
Industry-specific frameworks include HIPAA for healthcare, PCI DSS for payment card processing, and FedRAMP for cloud services used by federal agencies. Many enterprises adopt multiple frameworks, leveraging a unified risk management platform like Thoropass to streamline compliance across overlapping requirements while maintaining comprehensive security coverage appropriate to their specific risk profile.
How often should a company conduct cybersecurity risk assessments?
Cybersecurity risk assessments should operate on scheduled, event-triggered, and perpetual cycles to maintain an accurate risk profile. At a minimum, enterprises should conduct comprehensive formal assessments annually to evaluate their overall security posture against established frameworks and compliance requirements. However, this baseline should be supplemented with quarterly reviews and continuous monitoring of high-priority risks and critical systems to ensure controls remain effective.
What is the difference between cybersecurity risk management and vulnerability management?
Cybersecurity risk management and vulnerability management are complementary but distinct components of a comprehensive security program.
Risk management is the broader discipline that addresses the entire spectrum of security threats to an organization, including technical vulnerabilities, human factors, physical security concerns, and third-party risks. It involves identifying valuable assets, analyzing potential threats, implementing controls, and continuously evaluating the organization’s security posture against business objectives.
Vulnerability management is a subset of risk management that focuses specifically on identifying, classifying, prioritizing, and remediating technical weaknesses in systems, applications, and networks. It typically involves regular scanning, patch management, and configuration assessment activities that feed into the larger risk management program.
The key difference lies in scope and approach. Effective security programs integrate both disciplines, using vulnerability findings to inform risk-based decision-making.
CASE STUDY
How The Access Group reduced audit time by half and cut costs by 25% with Thoropass
.webp)
Related Posts
Stay connected
Subscribe to receive new blog articles and updates from Thoropass in your inbox.
Want to join our team?
Help Thoropass ensure that compliance never gets in the way of innovation.














.png)