Financial Technology (FinTech) drives repeatable, secure processes that promote fast, safe, and user-friendly transactions. It is one of the most complex and highly volatile regulatory landscapes with significant stakes for financial institutions and their customers. Adding to these complexities is the need to ensure compliance over multiple jurisdictions and the costs, in terms of both human resources and IT resources, associated with its maintenance, given that granular controls change continuously.
Compliance solutions that can scale dynamically in an automated environment are essential to a financial organization’s success. We’ll provide a comprehensive overview of the FinTech compliance landscape and show how DuploCloud and Thoropass can automate the lion’s share of work, drastically reducing the manual effort required by your team and putting your most seamless compliance journey within reach.
Why compliance is crucial in FinTech
Failure to pass compliance audits in almost any industry results in hefty fines and catastrophic damage to reputation. In FinTech, the risks are magnified exponentially.
- A high-profile data breach or hack can bring down even the most resilient and time-tested bank or brokerage, driving it to dissolution or bankruptcy. The loss of consumer or industry trust can resonate throughout financial markets, imperiling global stability.
- Failed audits generally result in even closer scrutiny by regulatory boards, increasing the risk of elevated operational costs amidst more frequent and rigorous audits.
- As FinTech companies often operate globally, non-compliance in one jurisdiction can have cascading effects across multiple regions, complicating international operations and regulatory relationships.
Building an audit and compliance roadmap
At the core of a successful compliance framework is a roadmap—a strategic plan for creating a closed-loop, predictable process for meeting and exceeding FinTech compliance standards that scale as your customer base expands. However, with so many frameworks and regulations, it can be hard to know where to begin.
Choosing the proper compliance framework
What should a FinTech company search for when building a foundational roadmap? How much should they invest in financial and human resources? How do you know if it’s a solution that will sync with your future needs?
- Analyzing the data you store and transmit – The type of customer data you store and transmit directly drives which compliance framework you aim to satisfy. Below are the two most common frameworks in FinTech.
- SOC 2 tests an organization’s internal controls over a security program and is the most generally sought-after standard. It provides checks and balances to prove to your customers that you’re securing their data in the manner you represent. For any product to be available in the US market, SOC 2 is a mandatory standard.
- PCI is the most common specific standard, focusing on network security, data protection, and card payment data access control. PCI compliance examines how cardholder data is protected, segmented, and stored. Depending on transaction loads, PCI audits have up to four levels, each bearing greater detail and scrutiny.
Any planning you do when creating a framework is pointless if that solution constantly requires a recurring investment to keep it in line with evolving standards and practices. Your customers may have more nuanced needs depending on the vertical markets in which they transact business, and understanding their security requirements is essential.
Cloud-based compliance implementation and optimization
Once a flexible and adaptive framework is in place, the next challenge is to ensure that it is implemented correctly in the most automated and least stressful way possible. This is where products like DuploCloud play a crucial role, as they help streamline the process and enhance efficiency. One key aspect of this implementation is understanding the CIA triad, which consists of three foundational pillars of network security essential for compliance standards.
The CIA (Confidentiality, Integrity, Availability) triad
The security triad is defined by:
- Confidentiality – Ensuring no one sees confidential information except those accessing it, shielding against data hacks and breaches.
- Integrity – Ensuring the data is legitimate. An example might be guarding against data doctoring that can be construed as fraudulent.
- Availability – Guarding against malicious (ransomware) and non-malicious availability events. The recent Crowdstrike attack is an excellent example of a non-malicious event that was the most significant disaster recovery effort in recent years.
Portfolio discovery and analysis
Transitioning the concepts of the CIA triad into practical applications begins with the discovery and analysis phase. This phase comprehensively examines an organization’s systems, data, and security requirements. The goal is to understand the existing setup, identify potential risks, and outline necessary enhancements. Below are the the components you are measuring against:
- Identity Management
- Network Security
- Access Controls
- Logging Strategies
- Data Hardening Vulnerability and Patch Management
- Endpoint protection Monitoring and Alerting
- Disaster Recovery
Aligning security foundations
Following the discovery phase, reviewing any additional contractual security obligations is essential. These requirements often complement unique regulatory and statutory obligations. For instance, while you offer PCI Level 3 protection by default, a client may need PCI Level 1. To build a robust security strategy, the following frameworks are employed:
- AWS Cloud Adoption Framework – Designed to help users migrate to the cloud, emphasizing business alignment, risk mitigation, operational efficiency, and other strategic benefits.
- AWS Well-Architected Framework – Assisting cloud architects in building secure, high-performing, resilient, and efficient infrastructure for their applications.
- AWS Shared Responsibility Model – Clarifying the responsibilities of AWS as a cloud service provider and the customer’s responsibilities.
DuploCloud provides insights to improve both the performance and efficiency of tasks in the customer’s realm of the shared responsibility model and, in the process, shift some of the workload to AWS based on those adjustments. The end goal should be to place the burden of responsibility where it makes the most sense from a business perspective.
Managing and implementing compliance controls
Compliance measures are included right from the beginning with DuploCloud. Although compliance controls differ vastly between standards, they are all exceedingly complex and depend on your size, workload, and many other variables. Addressing these requirements early on makes it easier to implement them later—you only use components that meet the necessary compliance criteria.
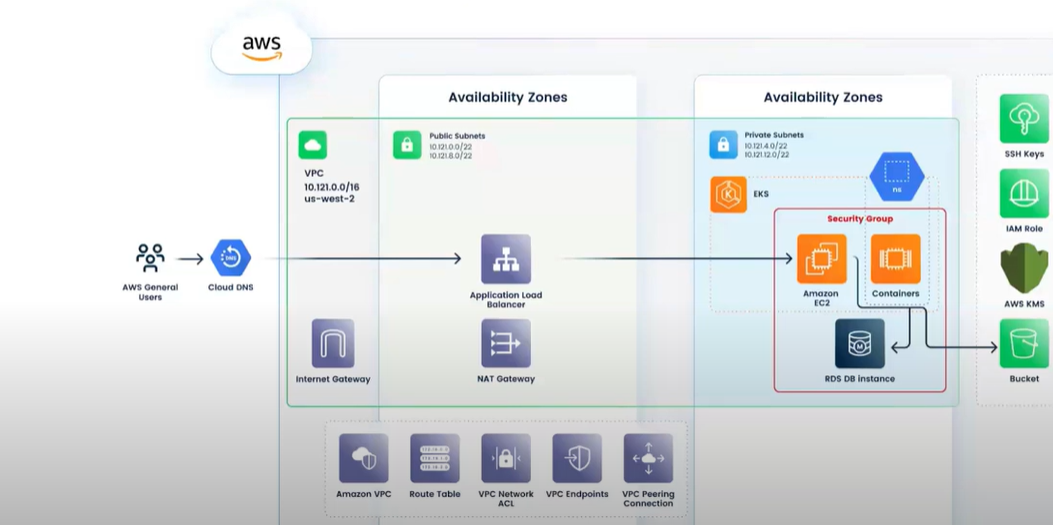
Comprehensive architectural and network documentation
DuploCloud provides a detailed diagram depicting the agreed-upon architecture and network configurations that align with your security and compliance needs. This ensures that all security and compliance requirements are clearly outlined. These mesh with controls that vendors such as Thoropass help you identify when building your Audit and Compliance Framework. Combining the expertise of Thoropass and DuploCloud ensures synchronicity between your audit-approved framework and the implementation of that framework.
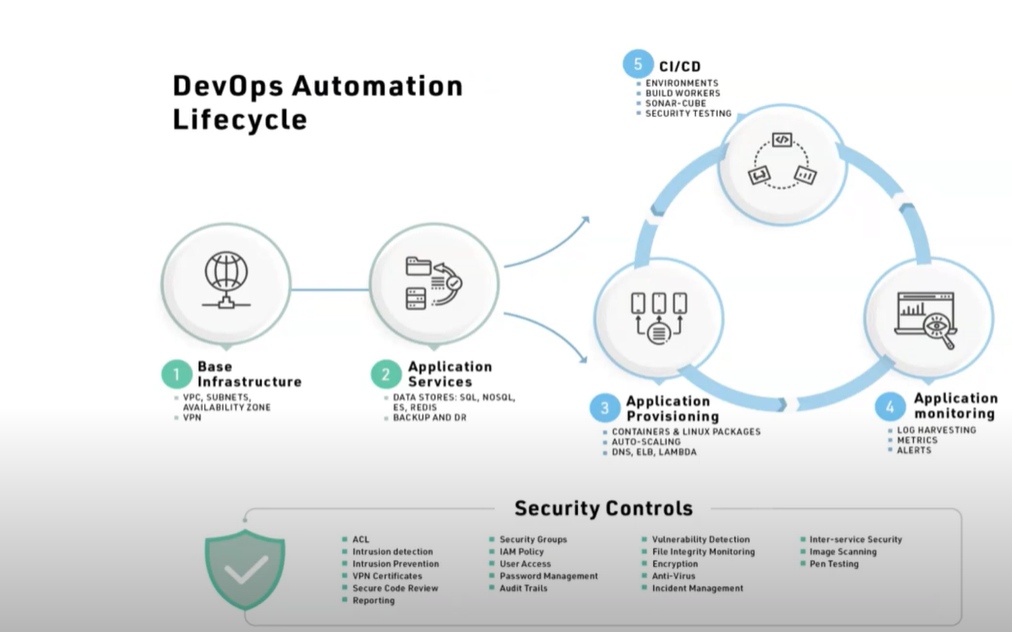
In addition, DuploCloud outlines and tunes your DevOps Automation Lifecycle Model, ensuring seamless integration of CI/CD, Application Provisioning, and Application Monitoring in the most efficient way possible.
Implementation phase
The implementation phase is crucial for turning planned strategies into operational realities. This phase is about setting up and configuring the necessary infrastructure and processes to ensure smooth and secure operations. It’s important because it lays the foundation for a reliable and compliant system, ensuring all elements work seamlessly and efficiently. Here’s a breakdown of the key steps involved:
- Defining the Landing Zone – Starting with a baseline built on AWS Best Practices, we establish MFA for users, delete default VPCs, close default security groups, ensure encryption of volumes in EC2, and so on. These actions provide a robust security foundation and prepare the environment for further customization.
- Defining the network architecture – We design and implement the network infrastructure. We create VPCs tailored to shared services while keeping them separate to meet compliance requirements. This segregation ensures that sensitive data is protected and the system’s design aligns with regulatory standards.
- Deploy, test, and tune – This step involves deploying the system components, followed by thorough testing to ensure everything functions correctly. We set up monitoring and logging systems to keep track of the system’s performance and potential issues. Disaster recovery policies are also implemented and rigorously tested to ensure the system can recover quickly in case of failure. We leave nothing to chance and validate all disaster recovery procedures to ensure readiness.
- Final production cut-over – The last step involves transitioning the system into a live production environment. We carefully schedule and execute the cut-over, ensuring minimal disruption. Our team monitors the process closely to address any issues that may arise, providing a smooth and successful transition to the entire operation.
Continuous improvement
DuploCloud and Thoropass work in tandem to ensure that your framework functions and evolves, ensuring you stay caught up. ISO-27001 Requirement 10.2 serves as a blueprint for continuous improvement. Included here are preparations for future audits, reviews of policies and controls, and reviews of security incidents. We want your security implementation to be dynamic, flexible, and resilient. If you’re out of compliance, you are immediately notified to remediate.
In addition, Thoropass specializes in integrating directly with your cloud platform, ingesting data that provides a detailed picture behind out-of-compliance incidents and guards against them in the future. In the past, this process was highly manual and fraught with potential error. Using Thoropass protects you against any threat that’s previously occurred going forward.

Related Posts
Stay connected
Subscribe to receive new blog articles and updates from Thoropass in your inbox.
Want to join our team?
Help Thoropass ensure that compliance never gets in the way of innovation.













.png)