Being compliant is a major priority across any organization that uses private data extensively to optimize business functions. Regulatory compliance and risk management are among the many cornerstones of a reliable business, and safeguarding sensitive information should never be undervalued. So, how can a company achieve this?
Enter — The HITRUST Common Security Framework.
What is HITRUST compliance?
But what is HITRUST, exactly? The acronym stands for the Health Information Trust Alliance, a non-profit company founded in 2007. HITRUST helps organizations manage digital information risk and protect sensitive data. Organizations can become compliant through HITRUST CSF Validation and by following data protection standards outlined by the HITRUST CSF.
HITRUST CSF is a globally utilized and recognized framework, having expanded its reach considerably since its inception sixteen (16) years ago. The company has branched out from its sole focus in the healthcare industry, with countless other industries now adopting its methods. The HITRUST CSF assurance programs and frameworks are relevant to international organizations of all sizes.
In this article, we’ll discuss a few key elements of the HITRUST CSF and highlight many of the important factors you should know about.
The HITRUST CSF
The HITRUST Common Security Framework – CSF was developed to manage security risks objectively and measurably. It originally lent itself specifically to healthcare information, but has since grown to include many other types of sensitive data across a variety of industries.
HITRUST CSF validation allows any organization, regardless of size, to prove that its systems meet the framework’s standards. All tiers of HITRUST validation call for many levels of assessment to receive a completed report, which ultimately helps companies improve their security posture and allow for greater stakeholder confidence.
The latest version of the HITRUST framework unifies many other authoritative, pre-existing security regulations and frameworks—such as NIST, GDPR, HIPAA, ISO 27001, and more. Think of the HITRUST CSF as an all-encompassing compliance package. With its risk-based approach, it helps organizations manage security challenges by implementing robust security and privacy controls.
HITRUST vs. HIPAA: What are the differences?
HITRUST is a comparatively newer compliance solution that has incorporated and enhanced many of the existing HIPAA (Health Insurance Portability and Accountability Act) guidelines and regulations. Though both HITRUST and HIPAA compliance are linked to HealthTech and healthcare organizations, they are far from identical.
HITRUST CSF is a framework that helps mitigate risk for an organization, developed by professionals in the security industry. HIPAA-mandated security controls, on the other hand, represent a full-fledged law built specifically to protect PHI (Protected Health Information). Thus, while any industry can implement HITRUST CSF, HIPAA is PHI-specific.
Achieving HITRUST compliance must also include an approved External Assessor or firm that has been authorized by HITRUST to certify that the framework is being followed.
On the other hand, internal or external reviews are used to demonstrate HIPAA compliance. Organizations that do not achieve HIPAA compliance run the risk of incurring a financial penalty if they are found in breach of certain regulatory requirements. Unlike HIPAA, HITRUST does not dole out financial penalties but can remove its certification which may put a dent into an organization’s trustworthiness amongst consumers.
HITRUST Scoring
HITRUST CSF scoring follows a mathematical calculation that transposes a raw score onto PRISMA-based maturity requirement statements.
- Are policies and procedures or standards in place?
- Is there a process or procedure to support the policy?
- Has it been implemented?
- It is being measured and tested by management to ensure it is operating?
- Are the measured results being managed to ensure corrective actions are taken as needed?
For each maturity level, the organization will indicate its level of compliance with the five options being:
- Non-compliant (0%);
- Somewhat compliant (25%)
- Partially compliant (50%)
- Mostly compliant (75%)
- Fully compliant (100%)
These statement scores are then averaged across a domain with the ideal score being 100% on Policy, Process, and Implementation. This score ensures the best chance that the organization will be HITRUST certified. While obtaining a high score is important, it is just as important to maintain the score over time as security and policy needs shift at both the organizational as well as industry level.
HITRUST vs. SOC 2: What sets them apart?
HITRUST CSF was originally introduced as a risk-solver for the healthcare industry, focusing on health records and ePHI (electronic protected health information) security. It has since evolved, now catering to a much wider range of industries. The intention behind SOC 2, on the other hand, is to help software companies and vendors exhibit their customer data protection via their security controls.
While both SOC 2 and HITRUST CSF tackle cybersecurity issues in cloud-based systems, their scopes are different in many ways. For starters, HITRUST is a risk-based framework, whereas SOC 2 is a compliance-based framework. The former assesses security controls based on a company’s maturity rating, whereas the latter tests security controls for overall efficacy.
HITRUST and SOC 2 also have differing certification expirations. HITRUST has different certification tiers with different expirations — the e1 (Essentials) and i1 assessment (Implemented) expire in 1 year, whereas the r2 assessment (Risk-based) expires in 2 years. On the other hand, SOC 2 operates on an annual basis, requiring re-examination every 12 months.
Who needs a HITRUST CSF Validation with Certification?
HITRUST CSF Validation can benefit just about any sector. Although originally formed with a focus on the healthcare industry, its security controls framework can be implemented across a variety of verticals.
While the HITRUST CSF Validation process is not technically mandated by law for any one industry, health insurance payers over the last decade have required their vendors to become HITRUST CSF Validated. As a result of this motion, HITRUST CSF Validation with Certification has become standardized in the healthcare industry.
Adhering to HITRUST requirements can benefit all organizations, as it establishes premium security standards for a company’s data and systems while putting key stakeholders at ease.
What are the HITRUST CSF control categories?
There are 14 HITRUST CSF control categories with 49 objectives and 156 control references (135 for security and 21 for privacy.), Each category has a designated objective (desired result) and multiple specifications (policies, guidelines, practices, etc.).
There are up to three levels of implementation for control requirements and there are over 1,900 requirement statements within the HITRUST CSF. However, based on risk and regulatory requirements, only a subset of the total list will be in scope for your organization.
Note: This list of controls is not in order of importance, as all controls are considered equally important.
- Information Security Management Program
- Access Control
- Human Resources Security
- Risk Management
- Security Policy
- Organization of Information Security
- Compliance
- Asset Management
- Physical and Environmental Security
- Communications and Operations Management
- Information Systems Acquisition, Development, and Maintenance
- Information Security Incident Management
- Business Continuity Management
- Privacy Practices
Each of the above HITRUST CSF controls are assessed based on the following five areas:
- Policy
- Procedure
- Implemented
- Measured
- Managed
HITRUST assessments: 19 domains of information security
The HITRUST CSF has 19 assessment domains of information security. These domains make it easier for teams to isolate concerns around data protection, and they are averaged based on the scores of the requirement statements to determine certification.
- Information Protection Program
- Endpoint Protection
- Portable Media Security
- Mobile Device Security
- Wireless Protection
- Configuration Management
- Vulnerability Management
- Network Protection
- Transmission Protection
- Password Management
- Access Control
- Audit Logging & Monitoring
- Education, Training & Awareness
- Third-Party Security
- Incident Management
- Business Continuity & Disaster Recovery
- Risk Management
- Physical & Environmental Security
- Data Protection & Privacy
Guide
A healthcare company's guide to HITRUST compliance
Discover how and why to get HITRUST certified
How long is HITRUST CSF Validation valid?
HITRUST Validated Reports with Certification retain their relevance based on the type of assessment — e1 and i1 are valid for 1 year, and r2 is valid for 2 years.
Over this time frame, if an interim review is conducted, there must be no breaches of the scoped controls since the initial HITRUST assessment.
What is the HITRUST CSF Validation with Certification cost?
HITRUST CSF certification is known for being rather expensive, given its depth and complexity. Costs can vary greatly from company to company, depending on the size and scale of your organization.
The range can be from $36,000 – $200,000 and will hit the higher end of the scale when a third-party auditor is involved. Conducting a readiness assessment without an External Assessor will trim down your fees, however, the level of security assurance will also decrease so it’s highly recommended you work with an Approved External Assessor when embarking on your HITRUST journey. It’s important to conduct a thorough assessment of your own needs and not jump to saving costs when it comes to protecting sensitive data.
That being said, if the HITRUST Validated Assessment and certification feel too pricey, any organization can still download the HITRUST CSF for free. So, if you decide that the fulsome HITRUST package exceeds your budget, do not worry—this framework PDF can still help you fulfill many important security goals. However, keep in mind that you may not get the same specific requirement statements in the free version, so while it can provide guidance, you’ll still need to do more work to become HITRUST CSF Validated.
How can my organization become HITRUST CSF validated through certification?
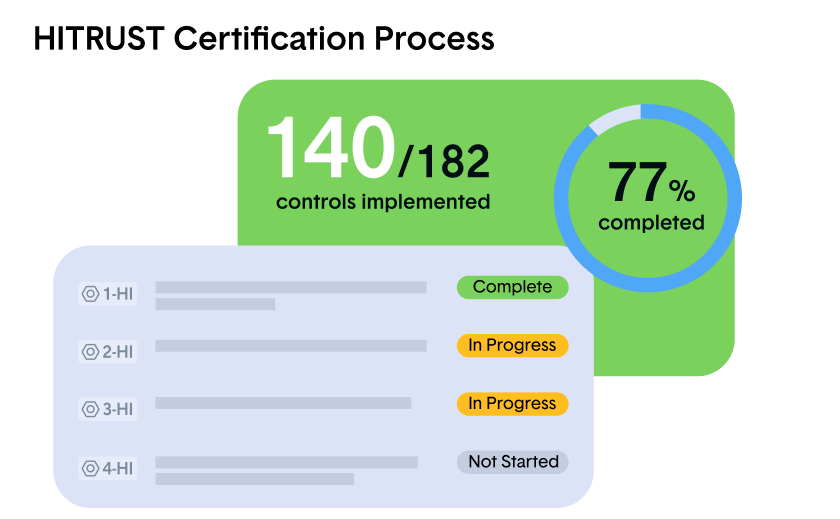
As previously mentioned, if you’d like to become fully HITRUST CSF Validated, an independent assessment will be performed by a HITRUST-approved External Assessor. The time it takes to complete the HITRUST certification process can take six (6) to twelve (12) months, depending on the nature of your organization.
Here is a breakdown of how to obtain HITRUST certification. These steps may help you feel more prepared for your assessment and understand what’s involved in the certification process. If these steps seem a little daunting, however, we would be happy to walk you through your assessment process.
1. Download the HITRUST CSF Framework (v11)
The simplest, most straightforward of all the steps!
2. Perform a readiness assessment
Through the HITRUST MyCSF platform, conduct one of the following: a HITRUST Risk-based 2-year Readiness Assessment (r2), a HITRUST Implemented 1-Year Readiness Assessment (i1), or a HITRUST Essentials 1-year (e1) Readiness Assessment. This step allows your company to self-assess under the HITRUST CSF Assurance Program, and from here you’ll learn which controls and requirements need implementation.
3. Get an external assessor
You’ll need to select a HITRUST Alliance licensed third-party auditor. The information gathered from your self-assessment, in combination with your security processes and controls, will all be thoroughly reviewed by your assessor based on the readiness tier you are seeking (e1, i1, or r2). As you mitigate the issues and close the gaps in your security, you move directly into HITRUST Validated Assessment.
4. Get validated
Your assessor’s assessment will be reviewed by the HITRUST Assurance Team.
5. Receive your HITRUST letter of certification
If you pass the final review by the HITRUST Assurance Team, you will then be issued your validated report and certification (only if certain criteria are met.)
The importance of HITRUST CSF compliance
Being HITRUST CSF certified is a key step in ensuring a viable, long-lasting business. And HITRUST is a surefire way to get you there. No company wants to be subjected to a cyberattack or security threat, so protecting your digital information and technology is critical.
With the pace of technology rapidly evolving and new threats arising every day, it’s important to make sure your systems are up to date and ready for the new challenges of the day. Keeping sensitive data and secure information shielded from harm is paramount. Planning for data breaches will prevent your company from becoming vulnerable.
HITRUST compliance helps organizations with internal and external risk management while keeping on top of new regulations, and ensuring that a high standard of data security is met. HITRUST protects sensitive information, reduces risk, and is always in step with the latest in cybersecurity best practices.
Being certified also demonstrates that your organization prioritizes digital security and privacy, which builds trust inside and out. HITRUST’s streamlined framework helps simplify compliance for your business, both now and in the future.
More FAQs
What is 'HITRUST compliant' or 'HITRUST certified'?
“HITRUST compliant’ or ‘HITRUST certified’ refers to an organization or system meeting the standards set by the HITRUST CSF (Common Security Framework), a comprehensive and certifiable framework developed to manage risk and ensure compliance with various regulatory and security requirements.
HITRUST is particularly important for industries handling sensitive data, like healthcare and finance, because it incorporates elements from multiple regulatory standards such as HIPAA, GDPR, and ISO, among others. It streamlines compliance across these frameworks, offering a unified approach to security and privacy controls.
To be HITRUST compliant, an organization must implement specific security and privacy measures, undergo assessments, and maintain continuous compliance through ongoing monitoring and updates.
This certification is seen as a high benchmark for organizations looking to demonstrate their commitment to data protection.
What is the difference between HITRUST and HIPAA?
The main difference between HITRUST and HIPAA is that HITRUST is a comprehensive, certifiable framework for managing data security, while HIPAA (Health Insurance Portability and Accountability Act) is a regulatory law that establishes baseline standards for protecting health information.
Here’s a breakdown of their key differences:
HIPAA
- Regulatory law: HIPAA is a U.S. federal law that mandates healthcare organizations, providers, and their business associates to protect and secure patients’ protected health information (PHI).
- Focus: It focuses on protecting the privacy and security of healthcare data.
- Scope: HIPAA applies only to entities handling healthcare data in the U.S.
- Compliance: Compliance with HIPAA is required by law, and there is no official certification for HIPAA compliance.
HITRUST
- Certifiable framework: HITRUST is a framework that helps organizations manage compliance with various regulations, including HIPAA, and offers HITRUST CSF certification.
- Focus: It provides a more detailed, prescriptive set of controls that address multiple standards beyond healthcare, including data security and privacy across industries.
- Scope: HITRUST is a broader framework, incorporating standards from various regulations like HIPAA, GDPR, and ISO, making it relevant to industries outside healthcare.
- Compliance: Organizations can seek certification to demonstrate they meet HITRUST standards, which often includes HIPAA compliance as part of the overall security controls.
In summary, HIPAA is a legal requirement for healthcare entities, while HITRUST offers a certifiable framework to help meet not only HIPAA but other regulatory standards as well.
What is the difference between HITRUST certification and SOC 2?
The main difference between HITRUST and SOC 2 lies in their focus, scope, and certification approach. HITRUST is a comprehensive, certifiable framework designed to help organizations manage compliance across multiple regulations, while SOC 2 is an audit and reporting standard focused on assessing an organization’s internal controls related to security and privacy.
Here’s a breakdown of the key differences:
HITRUST CSF certification
- Framework: HITRUST uses the HITRUST Common Security Framework (CSF), which integrates multiple regulatory and industry standards like HIPAA, ISO, GDPR, and more.
- Focus: Provides a comprehensive approach to data protection, risk management, and compliance across industries. It’s more prescriptive and detailed, offering controls that map to various regulatory requirements.
- Scope: Covers security, privacy, and risk management and is commonly used in healthcare, finance, and other sectors dealing with sensitive data.
- Certification: Organizations can achieve HITRUST CSF certification, which demonstrates they meet the required security and privacy controls. Certification is rigorous and requires ongoing compliance.
- Applicability: HITRUST is often chosen by industries with complex compliance needs, such as healthcare, because it provides a structured approach to regulatory compliance across multiple frameworks.
SOC 2 attestation
- Audit standard: SOC 2 (System and Organization Controls 2) is an auditing procedure developed by the AICPA (American Institute of CPAs) that evaluates an organization’s internal controls based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
- Focus: Primarily focuses on data security and internal controls for service providers. It is less prescriptive than HITRUST and more about verifying that an organization’s processes meet best practices for protecting data.
- Scope: SOC 2 applies to technology and service companies that handle customer data, particularly in the cloud services sector.
- Certification: SOC 2 results in an audit report (SOC 2 Type I or Type II) that outlines whether the organization’s controls were in place and functioning properly during a specific time (Type II) or at a specific point in time (Type I).
- Applicability: SOC 2 is commonly used by technology companies and service providers to demonstrate that their systems protect customer data according to industry standards.
Summary
- HITRUST provides a comprehensive framework for managing compliance across multiple regulatory standards and offers formal certification.
- SOC 2 is an audit that assesses an organization’s internal controls related to data security and results in a report but does not provide a certifiable framework.
While HITRUST focuses on detailed regulatory compliance across industries, SOC 2 is more about assessing and verifying security practices for service providers. Many organizations in highly regulated industries opt for HITRUST, while tech companies often choose SOC 2.
Is HITRUST for the healthcare industry?
Yes, HITRUST is highly relevant to the healthcare industry, but it is not limited to healthcare. HITRUST was originally developed to help healthcare organizations meet the stringent requirements of HIPAA (Health Insurance Portability and Accountability Act) and manage the security and privacy of protected health information (PHI). However, it has since evolved into a framework that applies across various industries.
How does HITRUST CSF determine an organization's compliance score?
HITRUST CSF scoring utilizes a mathematical calculation based on PRISMA-based maturity requirement statements, assessing five levels of compliance from non-compliant to fully compliant. Organizations strive for an ideal score of 100% on Policy, Process, and Implementation within each domain. This structured scoring method ensures a measurable approach to improving an organization's security posture and maintaining continuous adherence to the framework.
What is the significance of an External Assessor in HITRUST certification?
An independent HITRUST-approved External Assessor plays a critical role in the certification process by validating an organization's adherence to the framework. They review self-assessments, security processes, and controls to verify proper implementation. Engaging an External Assessor is highly recommended, as it significantly enhances the level of security assurance and is necessary for achieving full HITRUST certification.
How does HITRUST CSF integrate with other compliance frameworks?
The HITRUST CSF is designed as a comprehensive package that unifies numerous authoritative security regulations and frameworks into a single standard. It incorporates elements from widely recognized guidelines such as NIST, GDPR, HIPAA, and ISO 27001. This integration allows organizations to streamline their compliance efforts, manage security challenges efficiently, and demonstrate adherence to multiple regulatory requirements through a single, robust framework.
Beyond healthcare, which industries benefit from HITRUST CSF Validation?
While HITRUST was initially developed for the healthcare industry to protect electronic protected health information, its robust security controls framework has significantly expanded its applicability. Organizations across sectors dealing with sensitive data can now implement HITRUST CSF Validation to establish and demonstrate premium security standards for their systems and data.
Get Started with HITRUST
Your journey to HITRUST certification starts here.
The future of health tech is HITRUST! Whether you’re seeking e1, i1 or r2, Thoropass is your most comprehensive solution.
Related Posts
Stay connected
Subscribe to receive new blog articles and updates from Thoropass in your inbox.
Want to join our team?
Help Thoropass ensure that compliance never gets in the way of innovation.














.png)