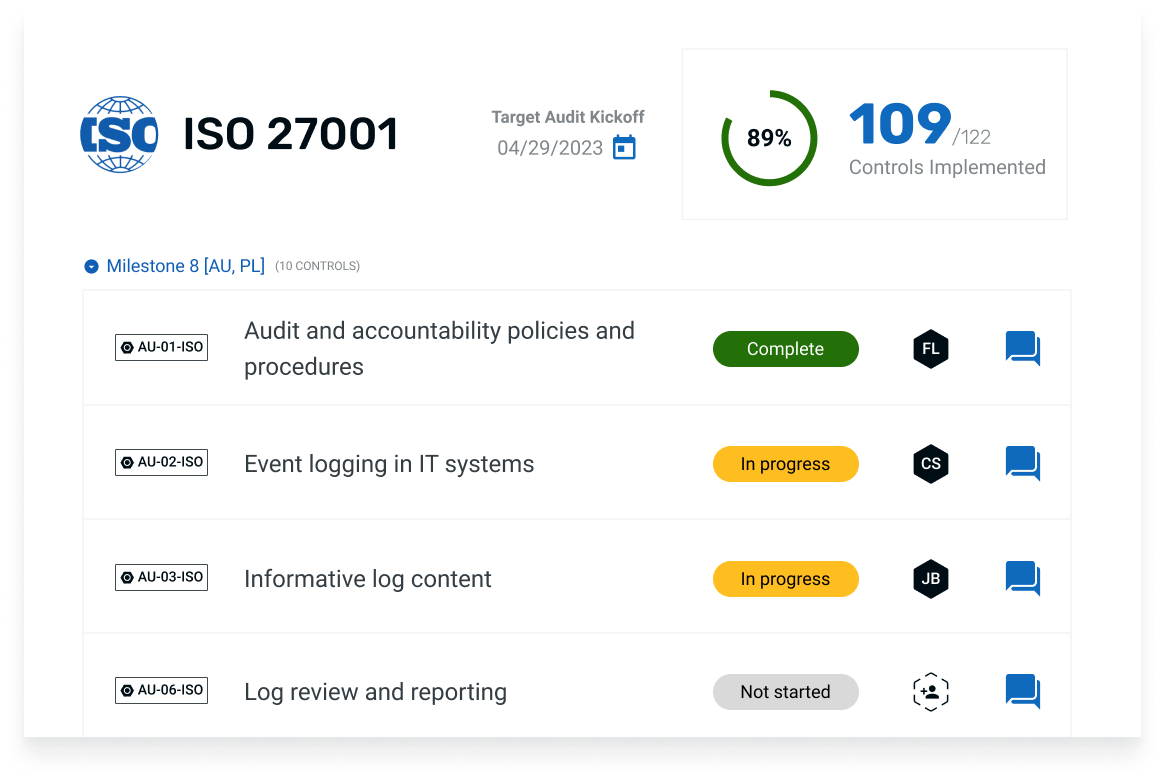
ISO 27001: 2022 controls (found in Annex A) are a set of policies and procedures that play a crucial role in reducing information security risks and are key for compliance with the ISO 27001 standards. To systematically manage these security risks and aim for Information Security Management Systems (ISMS) certification, organizations put these controls into action.
By embracing these measures, an organization not only safeguards its digital ecosystem but also demonstrates a strong dedication to rigorous information security management. The global standard provided by ISO 27001 offers a universally recognized framework that directs the application of such controls to maintain uniformity in information security practices worldwide.
Understanding ISO 27001 controls is fundamental to securing your business’s information assets. These controls offer a strategic blueprint for managing information security risks. From access control to organizational policy, this blog post details the adoption and execution of these critical measures, providing a clear path to robust cybersecurity practices and ISO 27001 compliance.
Key takeaways
- ISO 27001 controls are critical for organizations to systematically manage information security risks and for achieving Information Security Management System (ISMS) certification, with the framework addressing organizational, people, physical, and technological aspects of data protection.
- Implementing ISO 27001 controls requires understanding their structure and objectives, effectively managing access, ensuring human resource security, safeguarding physical environments, utilizing technological safeguards, and maintaining strong supplier risk management.
- Organizations must adopt a comprehensive approach to ISO 27001 implementation, including regular risk assessments, securing stakeholder engagement, and preparing for certification audits while leveraging technology to automate and streamline compliance tasks.
ISO 27001:2022 ISMS controls
The official ISO/IEC 27001:2022 standards document is broken into several sections, called clauses, and appendices called annexes. The ones you need to care most about and that we will dive into here are clauses 4-10 and Annex A.
There are 7 clauses (or requirements) listed in ISO 27001 —clauses 4 through 10 for establishing, implementing, maintaining, and continually improving the ISMS. These dictate what your ISMS should include to be an effective management system.
Clause 4: ISMS Organization and Context
Requirements 4.1-4.4 cover the scoping of your systems and how to design an ISMS, including:
- Clause 4.1 Understanding the organization and its context
- Clause 4.2 Understanding the needs and expectations of interested parties
- Clause 4.3 Determining the scope of the information security management system
- Clause 4.4 Information security management system
To complete both tasks effectively, your business will need to communicate why ISO 27001 is needed, the expectations of interested parties (customers, prospects, investors, etc.), and the scope that the ISMS should cover.
Clause 5: Commitment and Leadership
Clause 5.1-5.3 is short and to the point, covering leadership’s commitment to information security through an ISMS and the ISO 27001 standard. Clauses include:
- Clause 5.1 Leadership and commitment
- Clause 5.2 Policy
- Clause 5.3 Organisational roles, responsibilities, and authorities
Clause 5 as a whole defines roles and responsibilities within the organization for security and asks the organization to author an information security policy.
Clause 6: Risk Planning
With three parts, Clause 6 addresses planning for risk management and remediation.
- Clause 6.1 Actions to address risks and opportunities
- Clause 6.1.1 General
- Clause 6.1.2 Information security risk assessment
- Clause 6.1.3 Information security risk treatment
- Clause 6.2 Information security objectives and planning to achieve them
- Clause 6.3 Planning of Changes (note: this was new for ISO/IEC 27001:2022)
This requirement covers the information security risk assessment process and how the objectives of your information security posture may be impacted. This also includes clear documentation and risk treatment instructions and determining if your infosec program functions properly.
Clause 7: Communication and Resources
ISO 27001 requires a formal allocation of resources to the establishment, implementation, and demonstration of the ISMS, which is covered in Clause 7:
- Clause 7.1 Resources
- Clause 7.2 Competence
- Clause 7.3 Awareness
- Clause 7.4 Communication
- Clause 7.5 Documented information
- Clause 7.5.1 General
- Clause 7.5.2 Creating and updating
- Clause 7.5.3 Control of documented information
The resources must be competent, aware of their responsibilities, must communicate internally and externally about ISMS, and clearly document information to demonstrate compliance.
Clause 8: Operational Risk Assessment and Remediation
Clause 8 asks the organization to conduct regular assessments and evaluations of operational controls. These are a key part of demonstrating compliance and implementing risk remediation processes. This clause includes:
- Clause 8.1 Operational planning and control
- Clause 8.2 Information security risk assessment
- Clause 8.3 Information security risk treatment
Clause 9: Monitoring and Evaluation
Clause 9 defines how a business should monitor the ISMS controls and overall compliance. It asks the organization to identify which objectives and controls should be monitored, how often, who is responsible for the monitoring, and how that information will be used. More specifically, this clause includes guidance for conducting internal audits over the ISMS.
This clause also includes a requirement for management to review the monitoring at specific intervals to ensure the ISMS continues to operate effectively based on the business’ growth.
Clause 9 underwent the most change between ISO/IEC 27001:2013 and ISO/IEC 27001:2022 and now includes:
- Clause 9.1 Monitoring, measurement, analysis and evaluation
- Clause 9.2 Internal audit
- Clause 9.2.1 General (note: this was new for ISO/IEC 27001:2022)
- Clause 9.2.2 Internal audit program (note: this was new for ISO/IEC 27001:2022)
- Clause 9.3 Management review
- Clause 9.3.1 General (note: this was new for ISO/IEC 27001:2022)
- Clause 9.3.2 Management review inputs (note: this was new for ISO/IEC 27001:2022)
- Clause 9.3.3 Management review results (note: this was new for ISO/IEC 27001:2022)
Clause 10: Continual Improvement
Controls and requirements supporting the ISMS should be routinely tested and evaluated; in the instance of nonconformity, the organization is required to execute corrective action. It includes:
- Clause 10.1 Continual improvement
- Clause 10.2 Nonconformity and corrective action
This is key to any information security regulation, but ISO 27001 lays it out in the final requirements. The standard built continual improvement directly into it, which can be performed at least annually after each internal audit.
The essentials of ISO 27001 controls (Annex A): Four control themes
The framework of ISO 27001’s control structure is segmented into four main themes, each playing a critical role in establishing formidable information security. These encompass the following elements:
- Organizational controls: At the foundation of an organization’s data protection efforts are organizational controls which dictate its strategic formation along with policy-making and procedural execution.
- Number of controls: 37
- Control numbers: ISO 27001 Annex A 5.1 to 5.37
- Human resources (people) controls: Controls related to people ensure that there is clear communication about individual responsibilities regarding secure handling and protection of information assets.
- Number of controls: 8
- Control numbers: ISO 27001 Annex A 6.1 to 6.8
- Physical controls: Security measures concerning physical premises deal with protecting locations where sensitive information resides.
- Number of controls: 14
- Control numbers: ISO 27001 Annex A 7.1 to 7.13
- Technological controls: Technological controls focus specifically on employing advanced technical strategies and tools to shield digital data from threats.
- Number of controls: 34
- Control numbers: ISO 27001 Annex A 8.1 to 8.34
The goals and classifications of control are designed to encompass all aspects of information security.
For example: Controls in asset management include cataloging assets, appointing responsible owners, and implementing policies for proper usage. Objectives relating to access control are centered on maintaining authorized and safe entry to information resources while blocking any unauthorized admission. Meanwhile, human resource security is managed through a series of controls involving background checks before employment, defining the terms and conditions upon hiring, as well as providing training related to information security.
ISO 27001:2022 Annex A Controls
The standard includes controls listed in Annex A to support ISO 27001’s requirements. These controls cover the business’s technical operations and practices for securing information, people, and processes.
Because ISO 27001 is a prescriptive standard, ISO 27002 provides a framework for implementing Annex A controls. Compliance experts and auditors use this to determine if the controls have been applied correctly and are currently functioning at the time of the audit.
While the requirements define your ISMS, the controls in Annex A underpin the requirements with security and operational practices. ISO 27001 lists 93 controls, which largely deal with physical, technical, legal, and organizational security.
Below is a fairly comprehensive list of ISO 27001 Annex A controls.
ISO 27001:2022 Annex A 5: Organisational controls
- Number of controls: 37
- Control numbers: ISO 27001 Annex A 6.1 to 6.8
Organization controls are designed to establish a solid foundation for an effective Information Security Management System (ISMS).
These controls encompass various aspects of the organization’s policies, internal audits, and information security oversight. They aim to ensure that information security is systematically integrated into the organization’s processes and that there’s a clear governance structure for overseeing these efforts.
The full list of 37 controls in Annex A 5 includes:
- Annex A 5.1 Policies for information security
- Annex A 5.2 Information security roles and responsibilities
- Annex A 5.3 Segregation of duties
- Annex A 5.4 Management responsibilities
- Annex A 5.5 Contact with authorities
- Annex A 5.6 Contact with special interest groups
- Annex A 5.7 Threat intelligence (note: this was new for ISO/IEC 27001:2022)
- Annex A 5.8 Information security in project management
- Annex A 5.9 Inventory of information and other associated assets
- Annex A 5.10 Acceptable use of information and other associated assets
- Annex A 5.11 Return of assets
- Annex A 5.12 Classification of information
- Annex A 5.13 Labelling of information
- Annex A 5.14 Information transfer
- Annex A 5.15 Access control
- Annex A 5.16 Identity management
- Annex A 5.17 Authentication information (note: this was new for ISO/IEC 27001:2022)
- Annex A 5.18 Access rights
- Annex A 5.19 Information security in supplier relationships
- Annex A 5.20 Addressing information security within supplier agreements
- Annex A 5.21 Managing information security in the ICT supply chain (note: this was new for ISO/IEC 27001:2022)
- Annex A 5.22 Monitoring, review and change management of supplier services
- Annex A 5.23 Information security for use of cloud services (note: this was new for ISO/IEC 27001:2022)
- Annex A 5.24 Information security incident management planning and preparation
- Annex A 5.25 Assessment and decision on information security events
- Annex A 5.26 Response to information security incidents
- Annex A 5.27 Learning from information security incidents
- Annex A 5.28 Collection of evidence
- Annex A 5.29 Information security during disruption
- Annex A 5.30 ICT readiness for business continuity (note: this was new for ISO/IEC 27001:2022)
- Annex A 5.31 Identification of legal, statutory, regulatory and contractual requirements
- Annex A 5.32 Intellectual property rights
- Annex A 5.33 Protection of records
- Annex A 5.34 Privacy and protection of PII (personally identifiable information)
- Annex A 5.35 Independent review of information security
- Annex A 5.36 Compliance with policies and standards for information security
- ISO 27001:2022 Annex A 5.37 Documented operating procedures
ISO 27001:2022 Annex A 6: People controls
- Number of controls: 8
- Control numbers: ISO 27001 Annex A 6.1 to 6.8
ISO 27001 encompasses a range of controls regarding human resources security that are relevant before, during the employment period, and at the time when an individual’s role changes or they leave the company. The aim is to manage personnel in such a manner that it upholds information security within the organization.
Prior to hiring new staff members, organizations carry out background verifications and other precautionary procedures to validate if candidates align with their information security criteria. Once hired, employees must be regularly informed about their roles concerning maintaining information security through ongoing education on various safety measures and protocols.
When an employee’s position evolves or comes to an end within the company, there are essential processes that need implementation. These include formally updating or removing access rights as well as ensuring compliance with confidentiality agreements and securing company assets’ return.
The full list of 8 controls in Annex A 6 includes:
- Annex A 6.1 Screening
- Annex A 6.2 Terms and conditions of employment
- Annex A 6.3 Information security awareness, education and training
- Annex A 6.4 Disciplinary process
- Annex A 6.5 Responsibilities after termination or change of employment
- Annex A 6.6 Confidentiality or non-disclosure agreements
- Annex A 6.7 Remote working (note: this was new for ISO/IEC 27001:2022)
- Annex A 6.8 Information security event reporting
ISO 27001:2022 Annex A 7: Physical controls
- Number of controls: 14
- Control numbers: ISO 27001 Annex A 7.1 to 7.13
Physical security stands as a crucial counterpart to digital security in safeguarding information. The ISO 27001 standard encompasses distinct controls that guard against unauthorized entry and physical and environmental security threats, thus securing the organization’s assets on both fronts.
Policies like clear desk and clear screen are instrumental in thwarting unauthorized access to confidential data, tackling potential risks of such access, loss or damage not only within but also beyond regular business hours. In its effort to counter diverse environmental dangers, ISO 27001 defines strategies for the physical fortification and strategic placement of equipment critical for upholding information security and ensuring consistent operational effectiveness.
The full list of 14 controls in Annex A 7 includes:
- Annex A 7.1 Physical security perimeter
- Annex A 7.2 Physical entry controls
- Annex A 7.3 Securing offices, rooms and facilities
- Annex A 7.4 Physical security monitoring
- Annex A 7.5 Protecting against physical and environmental threats
- Annex A 7.6 Working in secure areas
- Annex A 7.7 Clear desk and clear screen
- Annex A 7.8 Equipment siting and protection
- Annex A 7.9 Security of assets off-premises
- Annex A 7.10 Storage media (note: this was new for ISO/IEC 27001:2022)
- Annex A 7.11 Supporting utilities
- Annex A 7.12 Cabling security
- Annex A 7.13 Equipment maintenance
- Annex A 7.14 Secure disposal or re-use of equipment
ISO 27001:2022 Annex A 8: Technological controls
- Number of controls: 34
- Control numbers: ISO 27001 Annex A 8.1 to 8.34
Implementing technological measures is a fundamental component of information security controls, designed to address different aspects related to safeguarding information in line with the ISO 27001 guidelines. An example of such importance is cryptography, which has been allocated its own dedicated control within this framework due to its role in ensuring the confidentiality, integrity, and availability of data.
Ensuring that the information security aspects of your business remain secure forms another critical aspect of these technological controls, incorporating strategies such as:
- The maintenance schedules for hardware
- Methods for securely discarding or repurposing equipment
- Defenses against malicious software
- Strategies for backing up data
- Protocols aimed at maintaining network security
These practices are essential in granting access only to those individuals who are duly authorized.
The full list of 34 controls in Annex A 8 includes:
- Annex A 8.1 User endpoint devices (note: this was new for ISO/IEC 27001:2022)
- Annex A 8.2 Privileged access rights
- Annex A 8.3 Information access restriction
- Annex A 8.4 Access to source code
- Annex A 8.5 Secure authentication
- Annex A 8.6 Capacity management
- Annex A 8.7 Protection against malware
- Annex A 8.8 Management of technical vulnerabilities
- Annex A 8.9 Configuration management
- Annex A 8.10 Information deletion (note: this was new for ISO/IEC 27001:2022)
- Annex A 8.11 Data masking (note: this was new for ISO/IEC 27001:2022)
- Annex A 8.12 Data leakage prevention (note: this was new for ISO/IEC 27001:2022)
- Annex A 8.13 Information backup
- Annex A 8.14 Redundancy of information processing facilities
- Annex A 8.15 Logging
- Annex A 8.16 Monitoring activities
- Annex A 8.17 Clock synchronisation
- Annex A 8.18 Use of privileged utility programs
- Annex A 8.19 Installation of software on operational systems
- Annex A 8.20 Network controls
- Annex A 8.21 Security of network services
- Annex A 8.22 Segregation in networks
- Annex A 8.23 Web filtering (note: this was new for ISO/IEC 27001:2022)
- Annex A 8.24 Use of cryptography
- Annex A 8.25 Secure development lifecycle
- Annex A 8.26 Application security requirements (note: this was new for ISO/IEC 27001:2022)
- Annex A 8.27 Secure system architecture and engineering principles (note: this was new for ISO/IEC 27001:2022)
- Annex A 8.28 Secure Coding
- Annex A 8.29 Security testing in development and acceptance
- Annex A 8.30 Outsourced development
- Annex A 8.31 Separation of development, test and production environments
- Annex A 8.32 Change management
- Annex A 8.33 Test information
- Annex A 8.34 Protection of information systems during audit and testing (note: this was new for ISO/IEC 27001:2022)

Recommended for you
A complete guide to ISO 27001 policies
Learn the importance of understanding, developing, and implementing these policies for a secure and compliant business environment.
Implementing ISO 27001 Controls: Steps to Success
ISO 27001 prescribes a plethora of controls and requirements. The implementation process can be laborious, but it is far less guesswork than similar frameworks, like SOC 2.
Each requirement or control has a practical application and a clear path to implementation, e.g. establishing the HR onboarding process or ensuring employees install antivirus software on their work devices.
The process of deploying ISO 27001 security controls requires a sequence of actions. Initially, an organization is to establish an implementation group led by a project leader proficient in information security matters.
Subsequently, this team devises a detailed plan for execution that encompasses setting objectives pertaining to security, formulating strategies and creating a risk register. It’s vital for the scope of the ISMS (Information Security Management System) to be clearly defined so as to understand the extent and limitations related to organizational information security.
The selection and tailoring of ISO 27001 prescribed controls are directed by an exhaustive risk assessment intended to align with specific threats and weaknesses faced by the entity.
Progressing involves putting into action a carefully devised risk treatment strategy, which incorporates:
- The successful deployment of chosen security measures
- Gaining support from stakeholders across various sectors
- Regular independent evaluations should also take place at set intervals or following significant changes within the company regarding its approach to maintaining information protection.
Entities on track for acquiring ISO 27001 accreditation need meticulous preparation for outside audits, beginning with preliminary assessments leading up to comprehensive scrutiny. Ascertaining effectiveness through internal auditing serves as both validation steps prior certification approval stage thereby solidifying defense mechanisms in place against potential breaches in data integrity.
Leveraging technology for ISO 27001 compliance
Software significantly enhances the efficiency of complying with ISO 27001 by automating the implementation of controls, continuous monitoring, and adherence to compliance standards. This automation reduces human error and streamlines processes.
Compliance-specific software tools like Thoropass deliver functionalities including starter templates and mappings for controls in line with ISO 27001, which facilitate the creation of policies and monitor the state of compliance.
Tips from the experts
Our compliance experts recommend starting with defining the ISMS scope and policies to support effective information security guidelines. Once this is established, it will be easier to digest the technical and operational controls to satisfy the ISO 27001 requirements and Annex A controls.
After you feel that your policies and controls have been defined, performing an internal audit will provide management with a clear picture as to whether your organization is ready for certification.
More FAQs
What are ISO 27001 controls?
Aiming to mitigate information security risks, ISO 27001 controls (Annex A) consist of a series of procedures and policies that are fundamental for sustaining an organization’s security while assuring adherence to the standards set by ISO 27001.
Not that there is a delineation between the clauses/requirements for ISO 27001 and Annex A controls. Annex A controls are a set of controls to help manage security risks, whereas the clauses/requirements are what are key for compliance with the 27001 standard for certification.
What’s the difference between clauses and controls for ISO 27001:2002?
Clauses 4-10 list every requirement an information security management system (ISMS) must meet before it can be ISO 27001 certified. Annex A lists 114 security controls that an organization can implement to meet those requirements.
What are the four themes of ISO 27001 controls?
ISO 27001 controls cover four key themes: organizational, human, physical, and technological dimensions to guarantee a holistic approach towards safeguarding information security.
How are access control mechanisms implemented in ISO 27001?
In ISO 27001, mechanisms for access control are put into effect by setting up an access control policy that is periodically reviewed, designating security roles and administering the management of access privileges.
How does ISO 27001 address physical and environmental security?
Specific controls within ISO 27001 are dedicated to ensuring physical and environmental security, safeguarding organizational assets from unauthorized entry or material harm. This includes the implementation of clear desk and screen policies as well as strategies for the physical safeguarding and proper placement of equipment.
What steps are involved in implementing ISO 27001 controls?
For the successful execution of ISO 27001 controls, it’s essential to assemble a dedicated team and create a strategic plan. This must be followed by executing a risk treatment plan. Conducting frequent independent reviews along with performing internal audits is vital to maintain compliance and assess the effectiveness of those controls.
Get Started with ISO 27001
Learn how Thoropass can help you get (and stay) compliant
Thoropass supports your success with a clear ISMS readiness roadmap, compliance automations, audit management, and experts to guide your certification journey.
Related Posts
Stay connected
Subscribe to receive new blog articles and updates from Thoropass in your inbox.
Want to join our team?
Help Thoropass ensure that compliance never gets in the way of innovation.














.png)