Receive quality, audit-ready reports as fast as you can say “penetration testing”
Pentesting? Yep, we do that too. Identify vulnerabilities, ensure readiness for compliance, and strengthen your security posture with top-quality test reports—all within a unified platform.
High Quality Testing
You won’t find generic, one-size-fits-all testing here. Thoropass scopes assessments to your unique environment, ensuring you can stay ahead of your unique cybersecurity risks and meet industry and regulatory expectations.
Trusted Expertise
Thoropass is CREST-accredited, considered the gold standard of pentesting. Our team of professionals bring deep technical knowledge, practical experience, and industry-leading certifications, ensuring a high standard of testing for all projects.
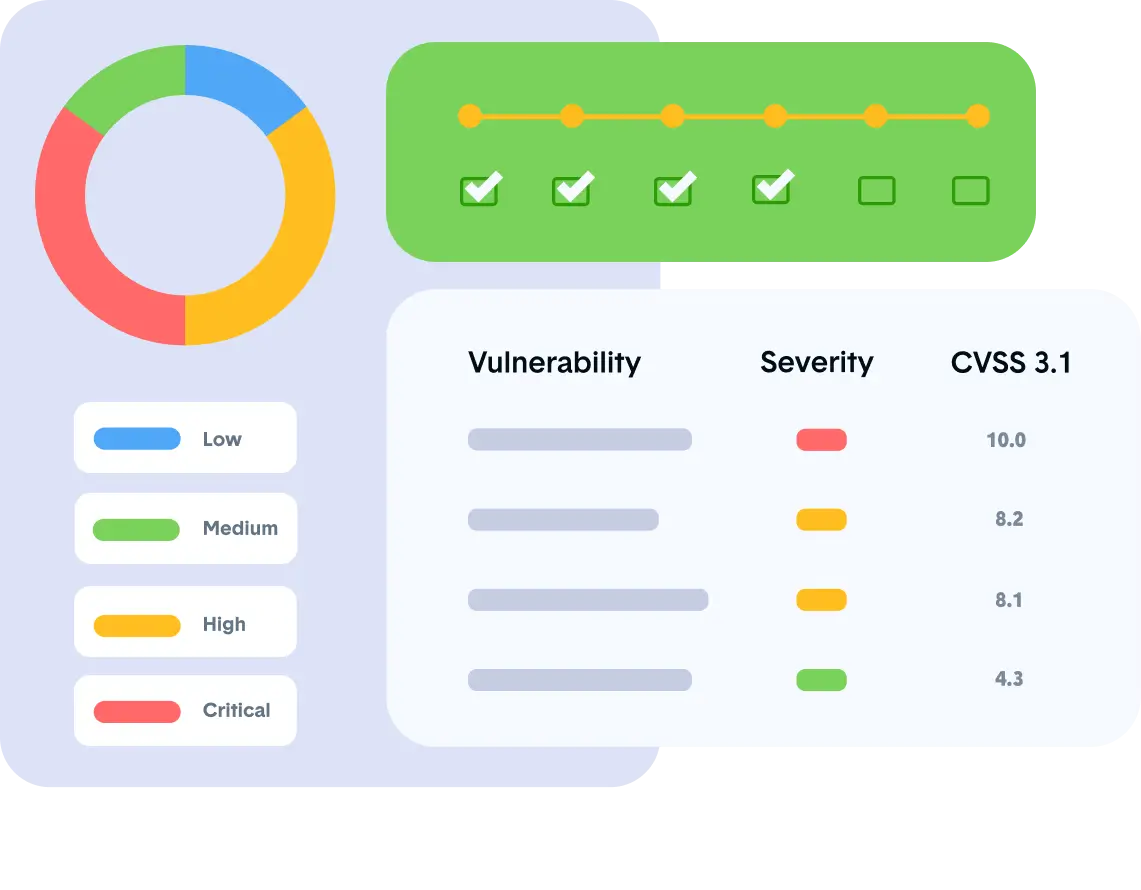
Actionable, Audit-Ready Reporting
Detailed, easy-to-understand reports with clear risk explanations and prioritized remediation steps. Our reports help your team not only fix vulnerabilities but also understand the root cause to improve long-term security.
The OrO Way
Thoropass’ integrated approach to compliance, audit, and pentesting delivers consistent, award-winning service and audit-ready reports that meet the needs of security teams and auditors alike. Consolidate your compliance and security efforts and save time integrating another third-party vendor.
Proactive, seamless, and comprehensive: Meet The OrO Way for Pentesting
Not only is it mandatory for PCI and HITRUST, it’s also the quickest and simplest path to meeting SOC 2, ISO, and other compliance requirements. With Thoropass, pentests become a strategic enabler for your business, boosting confidence in your cybersecurity strategy and ensuring compliance.
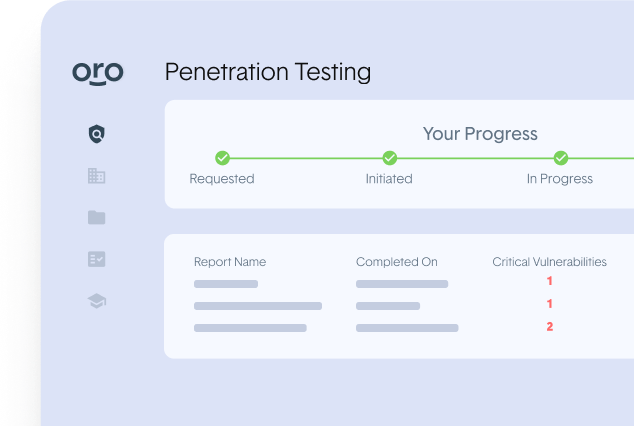
Audit-ready reports delivered in six simple steps
Our experienced pentesters follow a prescribed and thorough 6-step process.
Application Security
Web App Pentest
Identify and exploit vulnerabilities in your web applications to prevent hackers from breaching sensitive data.
Mobile App Pentest
Assess the security of your mobile apps by simulating real-world attacks to safeguard user data and privacy.
API Pentest
Test your APIs for security flaws that could expose your systems and data to external threats.
Web LLM
(AI Pentest)
Evaluate the security of your AI-driven web applications to prevent manipulating or breaching the integration with AI models.
Network Security
External Network Pentest
Simulate attacks from outside your network to uncover vulnerabilities that could be exploited by external hackers.
Internal Network Pentest
Identify weaknesses within your internal network that could be leveraged by malicious insiders or lateral attackers.
Network Vulnerability Scan
Automate the discovery of network vulnerabilities both externally and internally, ensuring no entry points are overlooked.
Network Segmentation Test (for PCI Lvl 1)
Verify that your network is properly segmented to protect the cardholder data environment in compliance with PCI DSS Level 1 standards.
Additional Solutions
Cloud Security Assessment (AWS / GCP / Azure)
Evaluate your cloud infrastructure for misconfigurations to ensure secure deployments in AWS, GCP, or Azure.
Microsoft 365 Security Assessment
Evaluate the security posture of your Microsoft 365 environment to identify potential risks and implement best practices for safeguarding your data and communications.
Social Engineering Assessment
Simulate real-world social engineering attacks (Phishing, Smishing, Vishing, OSINT) to evaluate employee susceptibility and improve your security awareness training.
Phishing Simulation Campaign
Test your organization’s readiness against phishing attacks by simulating a variety of phishing schemes to identify potential risks.
Ensure compliance with new and emerging AI frameworks
Identify new attack vectors and remediate potential security risks when deploying and managing Large Language Models (LLMs) with Thoropass’s new AI pentesting offering.





















.png)