Implementing ISO 27001 policies not only establishes a robust information security management system (ISMS) but also demonstrates compliance with international standards. In this blog post, you’ll learn the importance of understanding, developing, and implementing these policies for a secure and compliant business environment.
Key takeaways
- ISO 27001 policies provide many benefits, from protecting information assets to gaining a competitive advantage
- The policy scope outlines the application of policies across an organization and its information assets
- Automating ISO 27001 policy management can help organizations overcome resource constraints while staying compliant with standards
Understanding ISO 27001 policies & procedures
ISO 27001 policies are sets of requirements expected by executive management to be carried out by certain procedures. Policies and procedures are generally separate documents, with procedures outlining how an organization manages its data to satisfy the policies.
The main goal of ISO 27001 policies is to protect your organization’s information assets, ensure legal compliance, boost business reputation, and provide a competitive advantage. The ISMS also puts a strong emphasis on continual improvements, which involves regularly assessing, testing, reviewing, and measuring the performance of the ISMS as part of an organization’s broader strategy.
As an integral part of an Information Security Management System (ISMS), these policies cover a variety of aspects, including guiding principles, individual responsibility, intellectual property, and business continuity. We’ll cover the complete list of policies in the next section.
Implementing ISO 27001 policies also helps ensure the security of your organization’s information processing facilities and supports the principles of Confidentiality, Integrity, and Availability (CIA). By adopting these policies, your organization demonstrates its commitment to information security and adherence to international best practices.
Finally, achieving ISO 27001 certification provides independent proof that your company has implemented information security management systems that follow international best practices, including the protection of information processing facilities.

Recommended for you
How much does ISO 27001 certification cost?
Getting ISO 27001 certified is an investment of time and resources and how much can depend on the scale of your business and ISMS.
A complete list of ISO 27001 policies
To help you better understand the scope of ISO 27001, here is a comprehensive list of 25 policies that cover various aspects of information security management:
Information Security Policy
This policy outlines the framework for managing information security within the organization. It includes roles and responsibilities, risk management, and incident response procedures.
-> Data Protection Policy
This policy ensures that all personal and sensitive data is handled and stored securely and in compliance with relevant laws and regulations.
-> Data Retention Policy
This policy dictates how long data should be held and when it should be destroyed, in accordance with legal and business requirements.
Access Control Policy
This policy governs who has access to what information within the organization. It includes user registration, privilege management, and password management procedures.
-> Asset Management Policy
This policy is about the management of assets from acquisition to disposal. It includes asset classification, inventory, and disposal procedures.
-> Risk Management Policy
This policy guides the identification, assessment, and treatment of risks to the organization’s information assets.
Information Classification and Handling Policy
This policy provides guidelines for classifying information based on its sensitivity and dictates how each type of information should be handled.
-> Information Security Awareness and Training Policy
This policy ensures that all members of the organization are aware of security risks and know how to respond appropriately.
-> Acceptable Use Policy
This policy outlines what is considered acceptable behavior when using the organization’s information systems and services.
Clear Desk and Clear Screen Policy
This policy requires employees to keep their desks and computer screens clear of sensitive information when not in use.
-> Remote Working Policy
This policy governs how employees should secure information when working remotely.
Business Continuity Policy
This policy outlines how the organization will continue its critical operations during and after a disruptive incident.
-> Backup Policy
This policy provides guidelines for backing up data to ensure it can be recovered in the event of a data loss.
-> Malware and Antivirus Policy
This policy provides guidelines for protecting the organization’s systems from malware and viruses.
-> Change Management Policy
This policy ensures that all changes to information systems are managed in a controlled manner.
Third-Party Supplier Security Policy
This policy ensures that third-party suppliers adhere to the organization’s information security standards.
-> Continual Improvement Policy
This policy ensures that the organization’s information security management system is continually improving.
-> Logging and Monitoring Policy
This policy provides guidelines for logging and monitoring activities on the organization’s information systems.
Network Security Management Policy
This policy provides guidelines for securing the organization’s network infrastructure.
-> Information Transfer Policy
This policy provides guidelines for transferring information in a secure manner.
-> Secure Development Policy
This policy provides guidelines for developing secure software applications.
Physical & Environmental Security Policy
This policy provides guidelines for securing the organization’s physical premises, including protecting the organization’s information systems from environmental threats.
-> Cryptographic Key Management Policy
This policy provides guidelines for managing cryptographic keys.
-> Cryptographic Control and Encryption Policy
This policy provides guidelines for using encryption to protect sensitive information.
-> Document and Record Policy
This policy provides guidelines for managing documents and records related to the information security management system.
These policies provide a framework for organizations to safeguard their information assets and ensure their information is secure, reliable, and accessible.
Key components of ISO 27001 policies
The key components of an information security policy (per ISO 27001, clause 5.2 Policy:
- Appropriate to the organization’s purpose
- Includes information security objectives (or provides framework to set infosec objectives)
- Includes a commitment to satisfy applicable related infosec requirements
- Includes commitment to continual improvement of ISMS
The infosec policy needs to be documented, communicated, and made available to interested parties (as appropriate).
Understanding policy scope
Policy scope defines the applicability of the policy within the organization and its information assets. Accurately defining the scope is necessary for implementing appropriate security measures.
For instance, the Change Management Policy covers aspects like:
- Requests for change
- Approval
- Risk assessment
- Impact assessment
- Testing
The Document and Record Policy pays special attention to documents and records related to the information security management system (ISMS). It focuses on controlling these documents and records. It includes aspects like:
- Creating
- Updating
- Storing
- Version control
- Approval
- Document classification
Defining and communicating roles and responsibilities
Roles and responsibilities in an ISO 27001 information security management system include:
- Security leadership
- Security risk management
- Internal audit
- Control owners
- All employees
These individuals or teams, also known as interested parties, may be responsible for implementing, maintaining, and enforcing the policy.
The successful implementation and adherence to ISO 27001 policies heavily rely on everyone in the organization understanding their roles and responsibilities in the Information Security Management System.
A regular review and update process
A regular review and update process ensures that policies remain current and effective in addressing evolving security risks and organizational changes. This process involves assessing the effectiveness of the policies and making changes as needed.
ISO 27001 policies should be reviewed and updated at least once a year or when there’s a significant change in the organization’s environment, compliance requirements, internal audits, incidents or breaches, and transitions to new standards. This ensures the policies remain relevant and continue to protect the organization’s information assets effectively.
Implementing ISO 27001 policies
Developing and implementing ISO 27001 policies involves the following steps:
- Assessing information security risks
- Selecting and adapting policy templates
- Providing training and awareness
- Monitoring and auditing for compliance
Each of these steps merits a more comprehensive examination.
Assessing information security risks
In order to identify relevant policies and controls, assessing information security risks is a fundamental step in implementing ISO 27001 policies. The steps for assessing information security risks under ISO 27001 include:
- Defining the risk assessment method
- Making a list of information assets
- Spotting potential vulnerabilities and threats
- Assessing the likelihood and impact of each risk
- Judging the risks based on set criteria
- Choosing risk treatment options
Regular risk assessments help organizations ensure that their ISO 27001 policies stay relevant and effective in tackling current security risks and evolving organizational changes. This helps maintain compliance with ISO 27001 and demonstrates a commitment to information security.
Selecting and adapting policy templates
Policy templates can be customized to suit an organization’s specific needs and requirements, saving time and effort in policy development. Using ISO 27001 policy templates provides a standardized way to create important information security policies and procedures that meet ISO 27001 standards.
To adapt an ISO 27001 policy template to fit your organization’s needs, follow these steps:
- Define the scope of your information security management system (ISMS) and set clear objectives.
- Review existing policy templates and determine which ones are relevant to your organization.
- Customize the policy template by making the necessary changes and ensuring it reflects the unique aspects of your organization.
- Regularly review and update the policy to ensure it remains relevant and effective in keeping your organization secure.
Training and awareness
Training and awareness programs ensure that employees understand and adhere to the policies and their underlying principles. Some best practices for creating and implementing training and awareness programs include:
- Defining the objective and scope
- Creating and rolling out training content
- Using different training methods
- Maintaining the program
- Sending out regular reminders and reinforcement
- Measuring effectiveness
Investing in employee training and awareness enables organizations to:
- Cultivate a security-conscious culture
- Diminish the probability of security incidents
- Maintain compliance with ISO 27001
- Demonstrate a commitment to information security
Monitoring and auditing
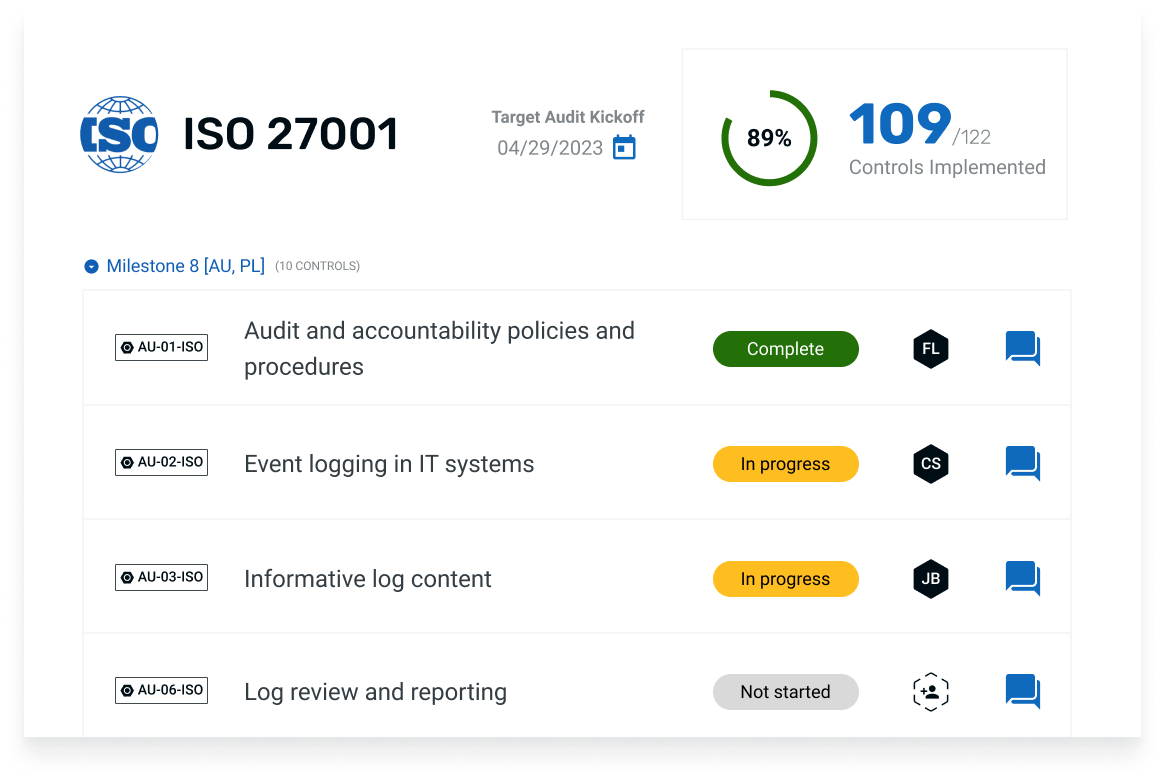
Regular monitoring and auditing of policy implementation help identify gaps and areas for improvement, ensuring ongoing compliance with ISO 27001. The process for monitoring and auditing ISO 27001 policies involves setting up a monitoring and auditing program, conducting regular reviews, and recording the outcomes.
Automation tools can be invaluable in simplifying policy management, including user access management and event logging access control. They can automate tasks such as:
- Gap assessment
- Monitoring security controls
- Updating documents
- Evidence collection
The use of automation tools allows organizations to save time, increase efficiency, and secure more accurate results in managing their ISO 27001 policies.
Effective implementation made easy
Implementing ISO 27001 policies is a critical step in enhancing your organization’s information security and demonstrating compliance with international standards.
Thoropass supports your success with a clear ISMS readiness roadmap, compliance automation, audit management, and experts to guide your ISO 27001 certification journey. Learn more here
By understanding the purpose and benefits of these policies, developing and implementing them effectively, and addressing common challenges, your organization can unlock the power of ISO 27001 policies for enhanced security.
Remember, a secure and compliant business environment is not only beneficial for your organization but also for your customers and stakeholders who place their trust in you.
More FAQs
What is the ISO 27001 access policy?
ISO 27001 Access Control Policy Principle ensures that users are only granted access to the information they need for their role, granting the least privilege possible.
What is the ISO 27001 audit policy?
The ISO 27001 audit policy involves an external auditor objectively reviewing the organization’s information security management system (ISMS) and verifying it meets the ISO/IEC 27001:2022 guidelines. Internal audits also promote a strong security posture by identifying non-conformities and vulnerabilities.
What is the acceptable use policy of ISO 27001?
The ISO 27001 Acceptable Use Policy defines the rules and procedures for acceptable use of information and other associated assets, protects users from illegal, discriminatory, and harassing activities, applies to all members and assets of an organization, and requires all users to read and sign off on the policy before accessing company systems.
What are the main benefits of implementing ISO 27001 policies?
ISO 27001 policies can help organizations improve information security, stay compliant with the law, increase their business reputation, and gain a competitive edge.
How often should ISO 27001 policies be reviewed and updated?
ISO 27001 policies should be reviewed and updated at least annually or whenever there are significant changes to the organization.
Get Started with ISO 27001
Learn how Thoropass can help you get (and stay) compliant
Thoropass supports your success with a clear ISMS readiness roadmap, compliance automations, audit management, and experts to guide your certification journey.
Related Posts
Stay connected
Subscribe to receive new blog articles and updates from Thoropass in your inbox.
Want to join our team?
Help Thoropass ensure that compliance never gets in the way of innovation.














.png)